In today’s digital world, it’s more important than ever to ensure the security of your Linux systems. One of the simplest and most effective ways to secure your systems is by blocking unwanted IP addresses. With iptables, you can easily configure your firewall to block IP addresses and prevent malicious traffic from reaching your system. This guide will walk you through the process of blocking IP addresses with iptables, providing step-by-step instructions and best practices to help you secure your Linux systems.
Iptables are recognizable to most system administrators. It has been around for a long and is enabled by default in the Linux kernel. We may use iptables to ban a single IP address, several IP addresses, or whole networks. This may be useful if you receive repeated port scans or witness failed unauthorized access in your log files. IP blocking is a more effective security measure.
Iptables may be used to block a specific IP address or a range of malicious IP addresses. Assume you are a system administrator in charge of infrastructure security. In that scenario, you may need to often block the IP addresses of the hosts attempting to penetrate your security. For example, you will need to utilize Iptables and the UFW firewall to block an IP address on a Linux server.
This guide will illustrate how to use iptables to restrict IP addresses.
Why block IP address?
Unwanted connections to our system might come from an IP address or a group of IP addresses. In such circumstances, we often block such IP addresses to improve security. For this reason, we can utilize iptables on Linux servers.
Using iptables to block IP addresses
Iptables is a Unix-based rule-based firewall that comes pre-installed in all Unix/Linux operating systems that manages incoming and outgoing packets.
This part will employ the iptables block IP firewall to block the IP address.
Restriction of Access to a Specific Port
You may also use the following syntax to block a specific IP address:
sudo iptables -A INPUT -s IP-ADDRESS -p tcp --dport port_number -j DROP
For example, to block the IP address 192.168.10.5 solely on port 100, use the command below:
sudo iptables -A INPUT -s 192.168.10.5 -p tcp --dport 100 -j DROP
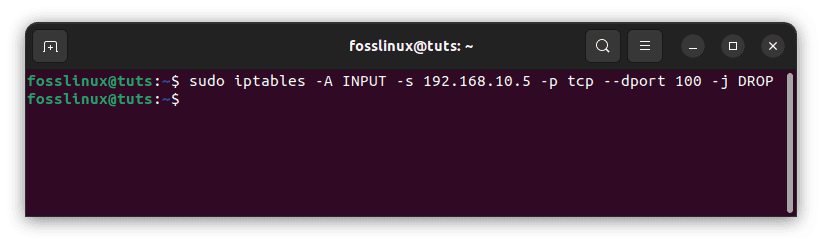
Block the IP address of a specific port
The following command will display the restricted IP address and port:
sudo iptables -L
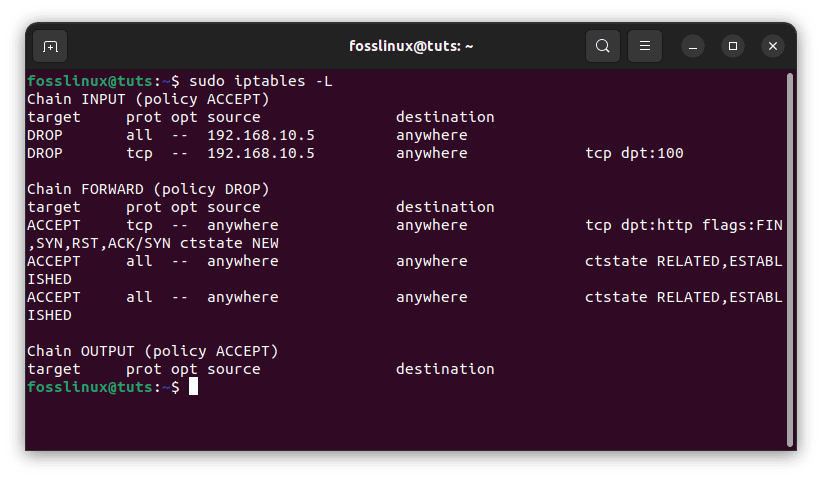
Check blocked IP address and port
Block All Port Access
Using the iptables block port may prevent an IP address from reaching your server.
sudo iptables -A INPUT -s IP-ADDRESS -j DROP
For example, the following command will completely block the IP address 192.168.10.5:
sudo iptables -A INPUT -s 192.168.10.5 -j DROP
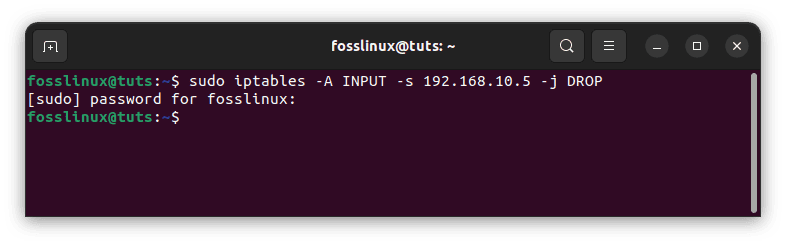
Block specific IP address
The following command will display the blacklisted IP address:
sudo iptables -L

Check blocked IP address and port
Save iptables Rule
The system will erase your iptables rule after resuming. As a result, you must permanently store the iptables rule on your system.
On CentOS/RHEL/Fedora, use the following command to save the iptables rule:
service iptables save
On Ubuntu/Debian, you must configure the iptables-persistent package in your Ubuntu/Debian system. To install and configure iptables-persistent, execute the following command:
sudo apt-get update -y && apt-get install iptables-persistent -y
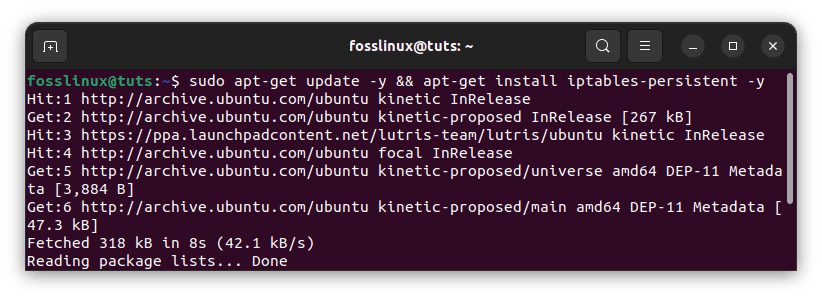
Install iptables persistent
Once installed, use the following command to save the iptables rule:
sudo service netfilter-persistent save
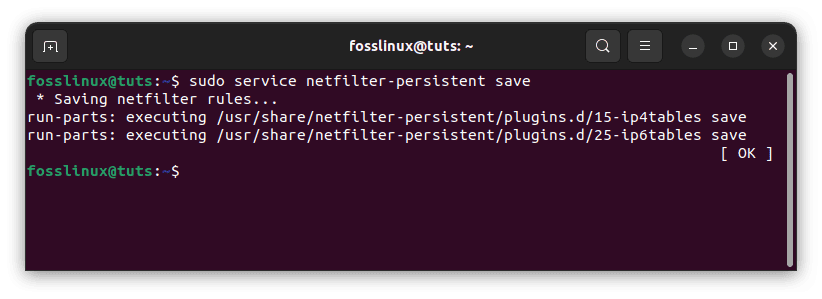
Save netfilter changes
Remove the DROP Rule.
If you wish to remove the rule that you added in the previous step, use the iptables drop command:
sudo iptables -D INPUT -s 192.168.10.5 -j DROP sudo iptables -D INPUT -s 192.168.10.5 -p tcp --destination-port 100 -j DROP
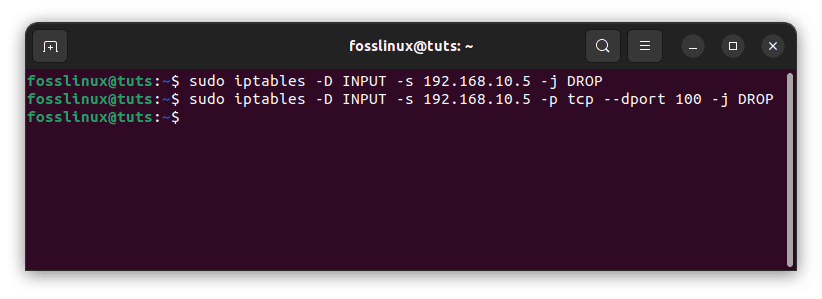
Drop appended rules
To save your modifications, execute the following command:
sudo service netfilter-persistent save
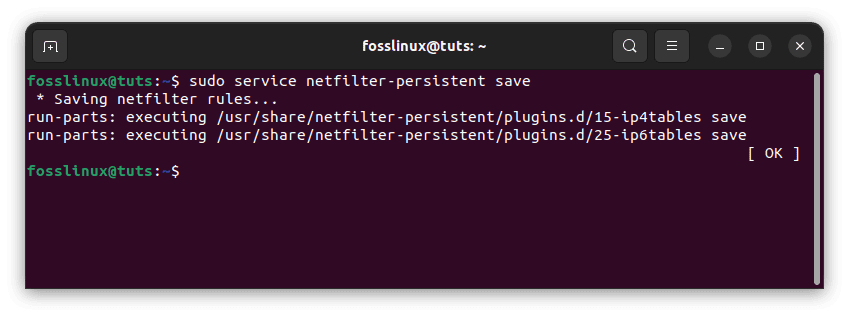
Save netfilter rules
Conclusion
IP addresses are mostly used to link devices. For instance, if an IP address is causing problems for your device or website, you should block it. The technique may differ depending on the operating system, but the basic notion is the same. The above tutorial demonstrates how to block IP addresses using iptables on your Linux OS. The procedure is straightforward and usual. I hope you are now able to secure your server without any challenges. Please let me know if you encounter any challenges via the comments section below. Thanks for reading.