In today’s digital age, monitoring network traffic has become increasingly crucial for businesses and individuals. With the rise of cyber threats and attacks, being able to keep an eye on your network traffic can help you detect potential security breaches before they become a major problem. In this article, we’ll discuss using iptables to monitor and log network traffic for analysis.
Iptables is a powerful tool that comes built-in with most Linux distributions. It is used to configure the Linux kernel’s built-in firewall, which provides security against various network attacks. Using iptables to monitor your network traffic, you can track what is happening on your network and detect any suspicious activity.
Network security is an important concern for any organization, and monitoring network traffic is one of the key components of a comprehensive security strategy. Iptables is a powerful program that can control network traffic by filtering packets based on various criteria. In addition to filtering, iptables can also be used to log network traffic, providing a detailed record of all incoming and outgoing packets. This article will discuss configuring iptables to log network traffic, including the basics of iptables logging, setting up log files, and some practical examples of monitoring network traffic.
Basics of iptables logging
Iptables logging is a feature that allows you to log network traffic that matches a specific rule. When a packet matches a logging rule, iptables will write a log message to the system log. The log message includes information about the packet, such as the source and destination IP addresses, the protocol type, and the port number. By default, iptables logs all matching packets, which can quickly fill up the system log. To avoid this, you can use the “–limit” option to limit the rate at which log messages are generated.
Examine the existing iptables rules
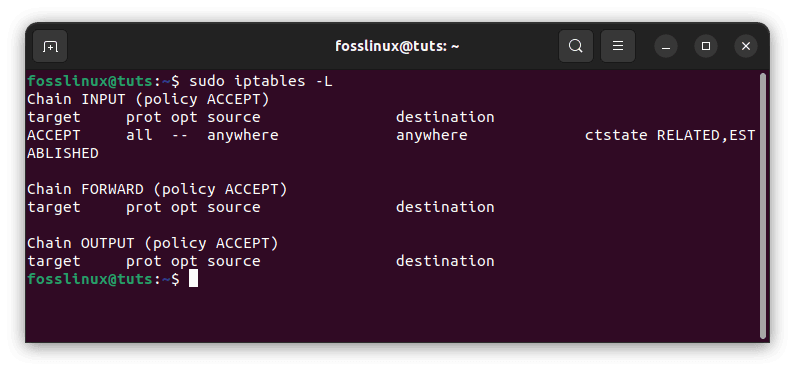
Before we begin, it is critical to understand the current iptables rules on your system. Enter the command below into the terminal to accomplish this:
sudo iptables -L
List current iptables rules
This command displays the current iptables rules, along with any logging rules.
Setting up log files
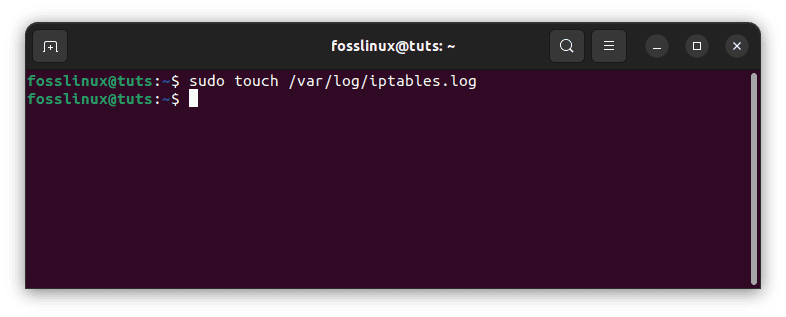
You must set up a log file to configure iptables to log network traffic. The log file can be any file written to by the system, such as a regular file or a named pipe. To create a log file, you can use the following command:
sudo touch /var/log/iptables.log
Create a log file
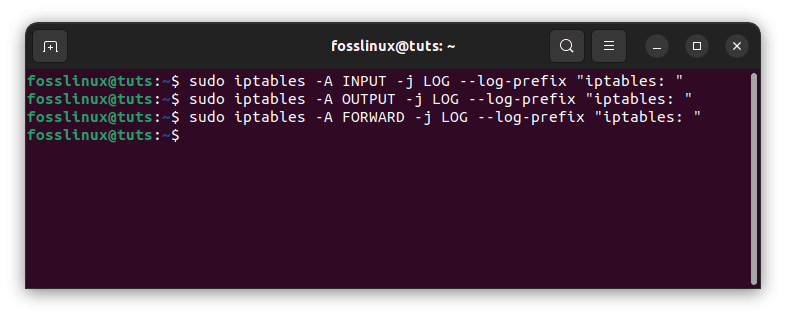
This command will create a new file called “iptables.log” in the “/var/log” directory. You can then configure iptables to write log messages to this file by adding a logging rule to the appropriate chain. Next, you must configure Iptables to write network traffic information to this log file. This can be done using the following commands:
sudo iptables -A INPUT -j LOG --log-prefix "iptables: " sudo iptables -A OUTPUT -j LOG --log-prefix "iptables: " sudo iptables -A FORWARD -j LOG --log-prefix "iptables: "
Allow iptables to write network traffic
These commands will log all incoming, outgoing, and forwarded network traffic and append the prefix “iptables: ” to each log entry.
The following command would log all incoming packets to the “/var/log/iptables.log” file:
sudo iptables -A INPUT -j LOG --log-prefix "iptables: " --log-level 4

Log all incoming packets
In this command, the “-j LOG” option tells iptables to log the packet, and the “–log-prefix” option specifies a prefix to be added to each log message. The “–log-level” option specifies the severity level of the log message, with a value of 4 indicating “warning” level messages.
Once you have configured Iptables logging, you can monitor your network traffic. You can view the log file using the following command:
sudo tail -f /var/log/iptables.log
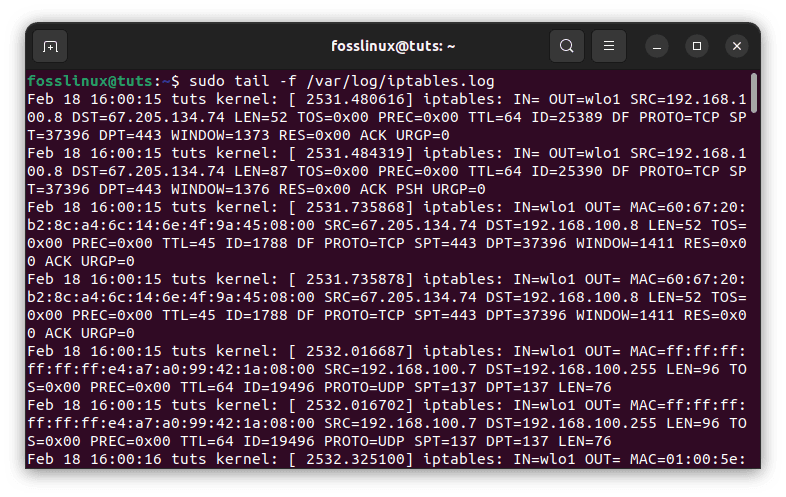
Monitor your network traffic
This command will display the last 10 lines of the log file and continuously update it as new entries are added. You can use this command to monitor your network traffic in real-time.
In addition to monitoring your network traffic in real-time, you can also use iptables logging to analyze past network traffic. For example, search the log file for specific IP addresses or port numbers to see which devices or applications generate the most traffic. This information can help you optimize your network and identify potential security threats.
Iptables and logging practical examples
Here are some practical examples of how to use iptables logging to monitor network traffic:
Example 1: Log all incoming packets
To log all incoming packets to the “/var/log/iptables.log” file, you can use the following command:
sudo iptables -A INPUT -j LOG --log-prefix "iptables: " --log-level 4
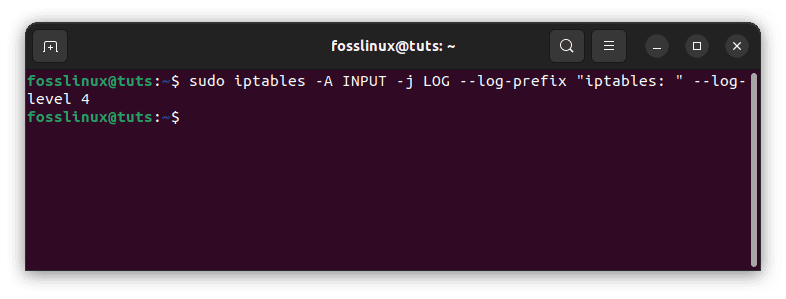
Log all incoming traffic packets
Example 2: Log all outgoing packets
To log all outgoing packets to the “/var/log/iptables.log” file, you can use the following command:
sudo iptables -A OUTPUT -j LOG --log-prefix "iptables: " --log-level 4
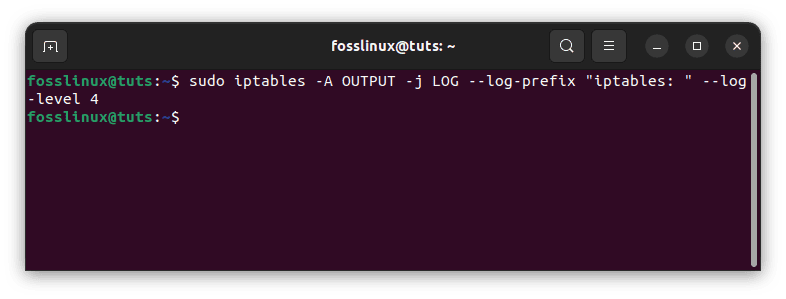
Log all outgoing packets
Example 3: Log all dropped packets
To log all dropped packets to the “/var/log/iptables.log” file, you can use the following command:
sudo iptables -A INPUT -j LOG --log-prefix "iptables: " --log-level 4 sudo iptables -A INPUT -j DROP
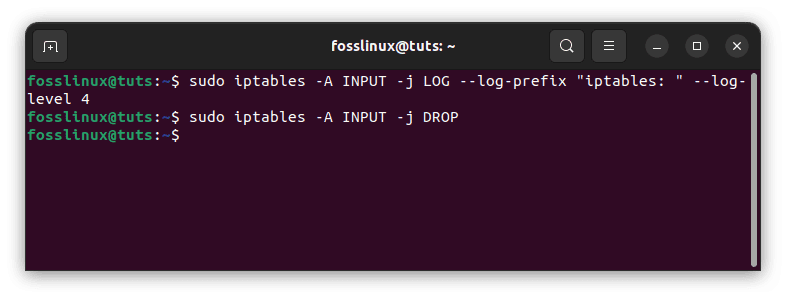
Log all dropped packets
In this example, the first rule logs all incoming packets, and the second rule drops all incoming packets. By logging the packets before they are dropped, you can get a detailed record of all dropped packets.
While the basics of Iptables logging are covered in the article, it’s important to note that more advanced options are available for logging and analyzing network traffic. For example, you can use iptables to filter network traffic based on specific criteria and then log only the filtered traffic. This can help reduce the amount of data written to the log file and make it easier to analyze the information.
Additionally, many third-party tools can be used to analyze iptables log files and provide more advanced reporting and visualization options. These tools can help you identify patterns and trends in your network traffic that may be difficult to spot using manual analysis.
Finally, it’s important to remember that Iptables logging is part of a comprehensive network security strategy. While it can be a powerful tool for monitoring and analyzing network traffic, it should be used in conjunction with other security measures such as intrusion detection systems, anti-virus software, and regular security audits. By taking a multi-layered approach to network security, you can help ensure your network’s and data’s safety and integrity.
Turn off logging
If you no longer want to log iptables traffic, remove the rule applied previously in this article. This may be accomplished by issuing the following command:
sudo iptables -D INPUT -j LOG
Disable logging
Conclusion
Configuring logging in iptables on a Linux server is critical to network monitoring and security. You should now have a basic grasp of configuring logging in iptables and utilizing logs to solve issues and improve safety if you follow the methods provided in this article. Note that logging in iptables is only one component of network security; it’s also essential to keep your system up to date, use secure passwords, and be mindful of other network vulnerabilities. Remember that logging is a dynamic process that must be monitored frequently to keep your system safe.
In this article, we have discussed how to configure iptables to log network traffic. By logging network traffic, you can get a detailed record of all incoming and outgoing packets, which can be used for security analysis and troubleshooting. We have discussed the basics of iptables logging, setting up log files, and some practical examples of network monitoring. In conclusion, monitoring network traffic is important to maintaining a secure and efficient network. Using iptables to log your network traffic, you can track what is happening on your network and detect potential security threats before they become a major problem. With the basics of Iptables logging and some practical examples of monitoring network traffic, you can start taking control of your network and keeping it secure. Thanks for reading.