Like other operating systems, Linux Mint generates logs that can provide valuable insights into system behavior, security incidents, and performance issues. However, managing system logs can be challenging, especially for system administrators and IT professionals.
This article will explore different aspects of managing system logs in Linux Mint, including how to locate, read, manage, and analyze them. Best practices for managing system logs and some of their security implications will also be discussed. While Linux Mint is known for its security features, it is not immune to threats like malware, viruses, and hackers. Here are 10 practical tips for securing your Linux Mint system.
Understanding system logs in Linux Mint
System logs are crucial to any operating system, including Linux Mint. They are files that contain detailed information about system events, errors, and warnings. System logs provide valuable insights into the system’s behavior, performance, security incidents, and other issues that may arise. In Linux Mint, several different types of system logs serve various purposes.
Kernel logs: These logs contain information about the kernel, which is the core component of the operating system. Kernel logs record system events related to hardware devices, drivers, and other low-level components.
Kernel logs
System logs: They contain general system information, such as system startup and shutdown events, system messages, and errors. They also provide information about system services and applications.
System logs
Authentication logs: These contain information about user authentication and authorization events. Authentication logs record successful and failed login attempts, user account changes, and password changes.
Authentication logs
Application logs: They hold specific information for applications running on the system. Application logs record app errors, warnings, and other third-party events.
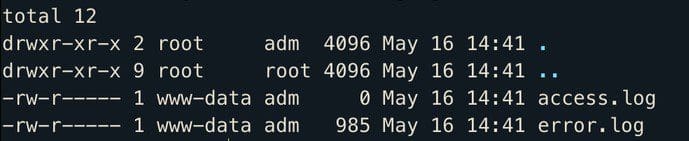
Application logs
Understanding the different types of system logs in Linux Mint is essential for effective log management. By analyzing these, administrators can identify and resolve issues, improve performance, and ensure the security and reliability of the system.
Locating system logs
Knowing where to find them in Linux Mint is essential to manage system logs effectively. System logs are stored in specific directories on the system, and there are various ways to access them.
The most common directory where system logs are stored is “/var/log/”. This directory contains a variety of system logs, including kernel, authentication, and application logs. Here, each file is named based on the type of log it contains. For example, the kernel log file is named “kern.log”, and the system log file is named “syslog”.
System logs stored in the var directory
Another important directory where system logs are stored is “/var/log/apt/”. It contains logs related to package management, including installation and update events. The log files in this directory are named based on the date of the event they record.
To access system logs using the command-line interface, use the “cd” command to navigate to the directory where the logs are stored. So, to access the “/var/log/” directory, run the following command in the terminal:
cd /var/log/
Accessing the log directory
Once in the directory, view the contents of the log files using the “less” or the “tail” command. “less” views the entire contents of a log file, while “tail” lists down the last few lines of that file. To view the contents of the “syslog” log file using the “tail” command, run the following command in the terminal:
tail -f syslog
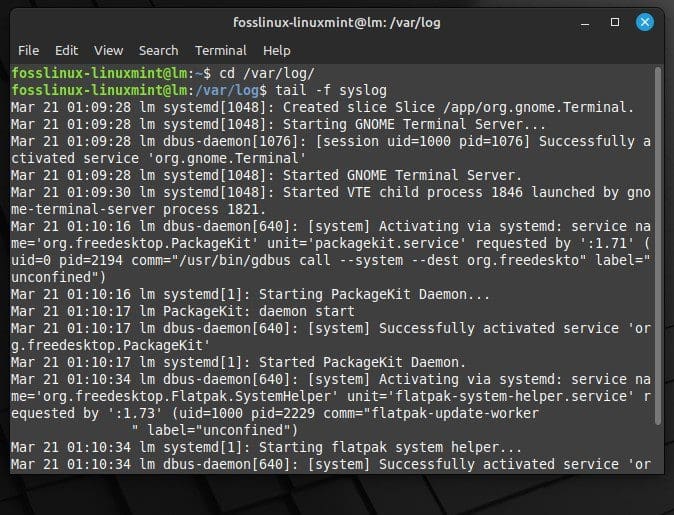
Viewing the contents of syslog file with tail
Doing so displays the last few lines of the “syslog” file and will continuously update as new entries are added.
Reading system logs
Once system logs have been located, the next step is to read them. Reading system logs can provide valuable information about system events, errors, and warnings that have already occurred.
The most common command-line tools used to read system logs are the “less” and “tail” commands. As described earlier, “less” is used to view the entire content, while “tail” is only for viewing the ending section. If you are in the home directory, it is also possible to employ these commands on the entire log path as follows:
less /var/log/syslog
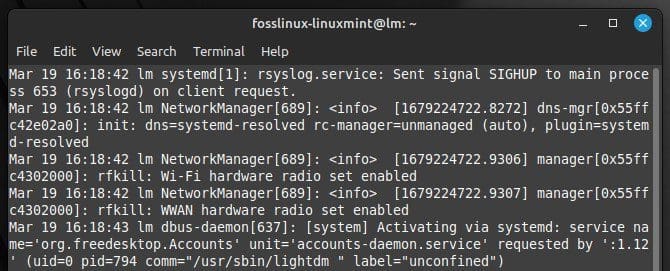
Viewing entire log contents with less
Doing so will display the entire contents of the “syslog” file. Use the arrow keys to navigate through the file and view different entries. Similarly, use the “tail” command as follows:
tail /var/log/syslog
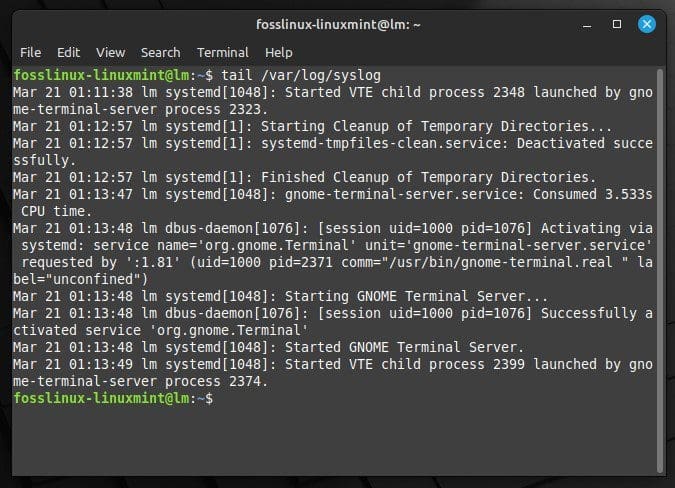
Viewing the last 10 logs with tail
This displays the last ten lines of the “syslog” file. Use the “-n” option to specify a different number of lines. To show the previous twenty lines, run the following command:
tail -n 20 /var/log/syslog
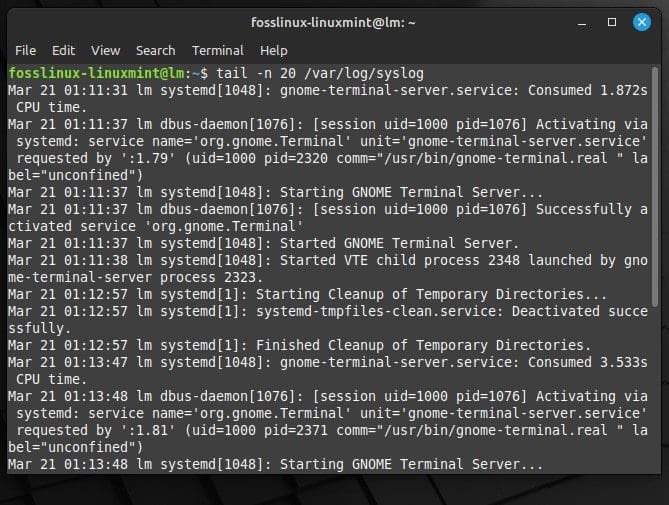
Viewing the last 20 logs with tail and -n option
In addition to these, you may also search for specific entries in system logs. To search for a specific entry, use the “grep” command. For all entries in the “syslog” file containing the word “error”, run the following command in the terminal:
grep "error" /var/log/syslog
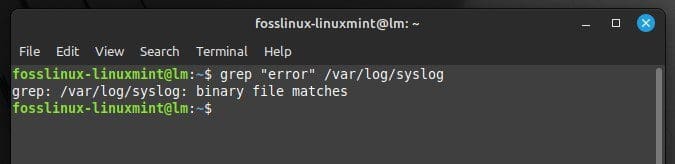
Searching for specific entries in system logs
This displays all entries in that file containing the word “error”. If required, use the “-i” option to perform a case-insensitive search.
Managing system logs in Linux Mint
Managing system logs has always been a crucial aspect of system administration. Over time, log files can consume a significant amount of disk space, and it is essential to manage them to prevent disk space from becoming exhausted.
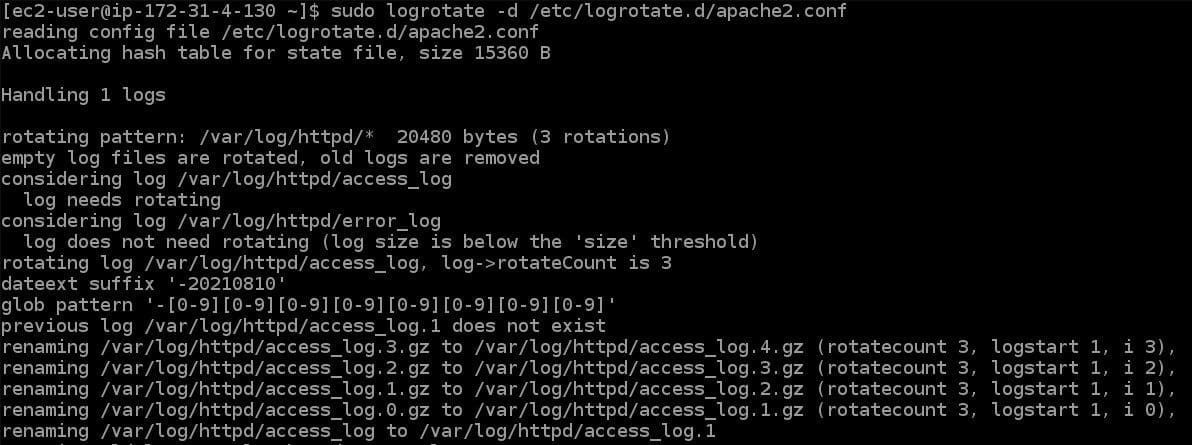
One way to manage system logs is to rotate them. Log rotation involves creating new log files and moving old log files to a different location. Linux Mint includes a log rotation utility called “logrotate”. To manually rotate logs, run the following command in the terminal:
sudo logrotate -f /etc/logrotate.conf

Rotating logs manually
This rotates all log files specified in the “/etc/logrotate.conf” configuration file. You may also pick a specific log file to rotate by running the following command:
sudo logrotate -f /etc/logrotate.d/log-sys
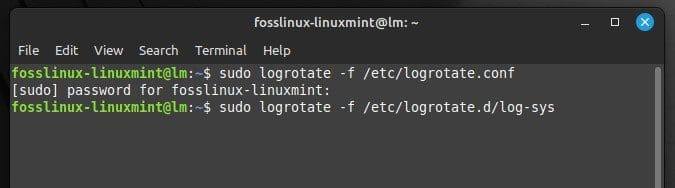
Rotating logs with a system file
This command only rotates the specified log file. Make sure to replace log-sys with the actual name of the file you want to rotate. Another way to manage system logs is to delete old log files. To delete files that are no longer needed, run the following command in the terminal:
sudo rm /var/log/log-sys
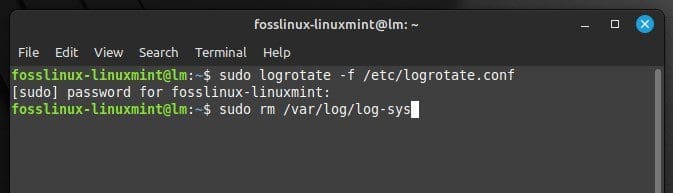
Deleting logs with a system file
Doing so deletes the specified log file. The “find” command can be used to delete log files older than a certain number of days. To delete log files in the “/var/log” directory that are older than 30 days, run the following command:
sudo find /var/log -type f -mtime +30 -delete
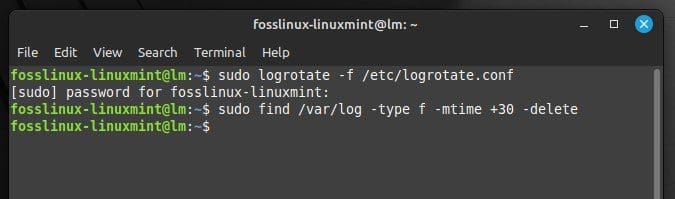
Deleting logs older than 30 days
This deletes all log files in that directory that have been stored for more than 30 days. Finally, it is also possible to compress log files to save disk space. To compress log files, run the following command in the terminal:
sudo gzip /var/log/log-sys
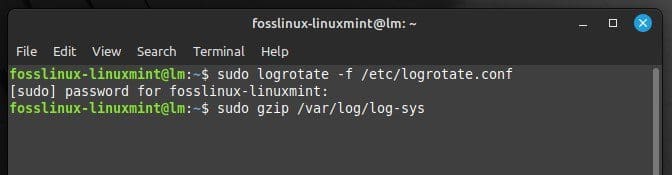
Compressing log files
This compresses the specified log file using the gzip compression algorithm. The “tar” command can also be used to compress multiple log files into a single compressed version. To compress all log files in the “/var/log” directory into a single file called “logs.tar.gz”, run the following command:
sudo tar -czf logs.tar.gz /var/log
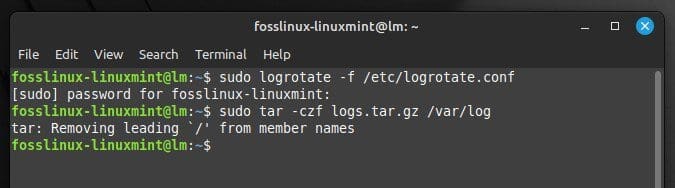
Compressing all log files into logs.tar.gz
Configure logrotate to run in the background using a cron job to manage logs automatically. To do this, create a new file in the “/etc/cron.daily” directory with the following content:
#!/bin/sh /usr/sbin/logrotate -f /etc/logrotate.conf
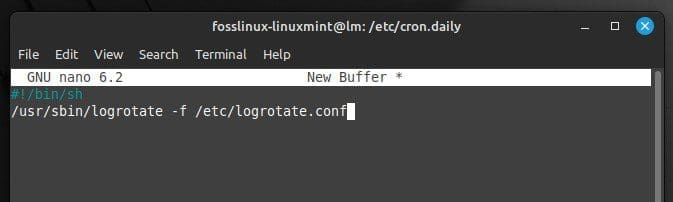
Managing logs automatically
This runs logrotate every day to rotate and manage log files regularly. Postfix is one of the most widely used free MTAs (Mail Transfer Agents). It is open-source and has been in active development since its inception. Learn how to install and configure Postfix on Debian.
Analyzing system logs
Analyzing system logs helps gain insights into system behavior and identify potential issues. One way to analyze system logs is to use log analyzers such as Logwatch and Logrotate.
Logwatch scans system logs and generates daily reports of system activity. To install it on your system, run the following command in the terminal:
sudo apt-get install logwatch
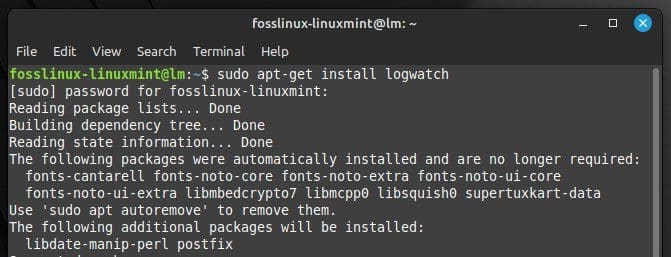
Installing Logwatch
Once Logwatch is installed, use it to generate a report by running the following command. This generates a report of your system activity for the previous 24 hours.
sudo logwatch
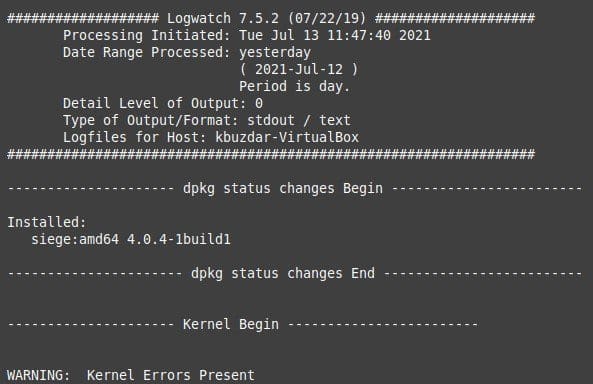
Generating a report with Logwatch
Logrotate is another analyzer that can be employed to gain insights into system behavior. It rotates logs and compresses them to save disk space, but it can also be configured to generate reports of system activity as well. To enable reporting in Logrotate, add the “report” option to the configuration file. For syslog, add the following lines to “/etc/logrotate.conf”:
/var/log/syslog {
daily
missingok
rotate 7
compress
delaycompress
notifempty
create 644 root adm
sharedscripts
postrotate
/usr/sbin/logrotate /etc/logrotate.d/rsyslog >/dev/null 2>&1 || true
endscript
report /usr/sbin/anacron -s
}
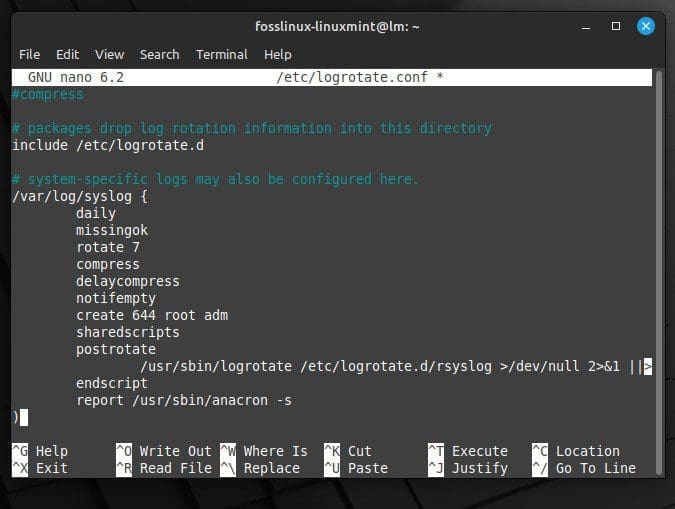
Adding the report option to the configuration file
You also have the option to analyze system logs manually. To do this, look for patterns and anomalies in the log files. Search for error messages, warnings, and other messages indicating potential issues. Also, look for patterns in system behavior, such as spikes in resource usage or unusual network activity.
Security considerations
System logs contain a wealth of information about system activity but pose several risks. One of the primary security considerations regarding system logs is protecting sensitive information. They can contain sensitive information such as usernames, passwords, IP addresses, and other confidential data. To protect this information, you must ensure that logs are stored securely, and access is restricted only to authorized personnel.
Restricted log access
You can monitor system logs for security incidents such as attempted unauthorized access or malware infections. Monitoring these can help identify potential security breaches and allow for quick action to be taken. Compliance with security regulations is also quite important when managing system logs. For example, organizations must comply with the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). These may require logs to be retained for a certain period of time, encrypted, or monitored regularly.
Monitoring system logs on Linux Mint
You should also take steps to secure the logging infrastructure itself. This includes securing access to the log files and ensuring the software is up-to-date and free from potential vulnerabilities.
Best practices for managing system logs
To effectively manage system logs in Linux Mint, you should follow some best practices that optimize performance, ensure security, and facilitate automation. The first step is to configure log settings. This includes setting appropriate log levels, defining log file sizes, and specifying the retention periods. Also, configure them to be encrypted and stored in secure locations.
Encrypted system log files
Automate log management tasks such as rotation and archiving. Ensure that log files are managed consistently and that space is efficiently utilized. Implement log monitoring and analysis to identify security risks and performance issues. Use log analyzers like Logwatch and Logrotate to gain insights into the system behavior and identify potential problems before they become critical.
Automated system log management
Ensure that log files are backed up regularly and that backups are stored securely. This guarantees that log files are not lost in a system failure. Finally, always adhere to relevant security regulations, regularly reviewing and analyzing all log files on the system, especially if you are a network administrator.
Conclusion
Managing system logs helps monitor system performance, troubleshoot issues, and maintain security. This article covered various aspects such as understanding system logs, locating and reading them on your Linux Mint device, managing them effectively, and some security considerations. By following these best practices and adhering to relevant security regulations, you can ensure your system logs are optimized for performance, secure from potential threats, and compliant with industry standards. Are you looking to boost your productivity by unlocking the full potential of a Linux-based system? Master the art of Ubuntu keyboard shortcuts with this comprehensive guide.