When I started my Linux journey, I often used to find myself grappling with the complex concepts of its diverse ecosystem. But over the years, I have developed a deep love for it, especially for Ubuntu, and one of its pivotal features, SSH keys.
SSH keys have made my life simpler and more secure, significantly reducing the hassle of passwords. Yet, they can be a little tricky to set up, particularly for new users. So today, I’d like to guide you on how to set up SSH keys on Ubuntu. And yes, we’ll do this with a practical example.
But first, let’s get a bit more context.
SSH Keys – Why do they matter?
SSH, or Secure Shell, is a cryptographic network protocol used for secure network communications and remote command execution. To put it plainly, it’s a way of accessing your server remotely. Now, as much as I love my passwords (yes, I’m a bit old-fashioned that way), using a password for SSH can be a nuisance. And, here’s where SSH keys come to the rescue.
SSH keys offer a more secure way of logging into a server. They provide a pair of cryptographic keys – a public and a private key. The public key can be shared with anyone, but the private key must remain secret. In a nutshell, SSH keys provide a secure, password-less login. To me, they are like a magic spell in the vast world of Ubuntu!
Setting up SSH keys on Ubuntu – A step-by-step guide
Let’s now dive into setting up SSH keys on Ubuntu. Make sure you have Ubuntu installed and running on your computer. If not, it’s time for a quick installation. But remember, the process can be addictive – there’s something oddly satisfying about seeing Ubuntu come to life! Note that the below screenshots are from Pop!_OS, which is an Ubuntu-based Linux derivative. The steps are exactly the same on Ubuntu.
Step 1: Generating the SSH key pair
Open your terminal using the shortcut Ctrl + Alt + T. Believe me, this shortcut has become second nature to me over time!
In the terminal, type in the following command:
ssh-keygen -t rsa -b 4096
This command tells the system to create a new SSH key using RSA encryption with a 4096 bit size. This size of the key is my personal preference for a balance between security and performance, but feel free to use a different size if you prefer.
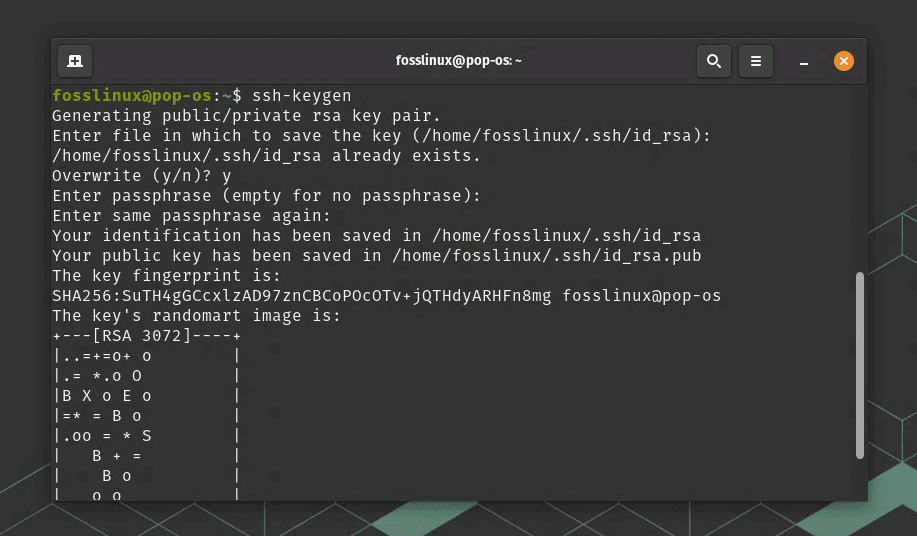
Generating SSH key
Upon executing the command, you’ll be asked where to save the key. If you’re happy with the default directory (~/.ssh/id_rsa), press Enter.
Next, you’ll be asked to enter a passphrase. While it’s optional, I highly recommend using one for added security.
Step 2: Copying the public key to the server
After the key pair generation, it’s time to place the public key on the virtual server. I’ll use the ssh-copy-id command, but there are many ways to accomplish this. In my opinion, this command is a quick and straightforward solution.
ssh-copy-id username@remote_host
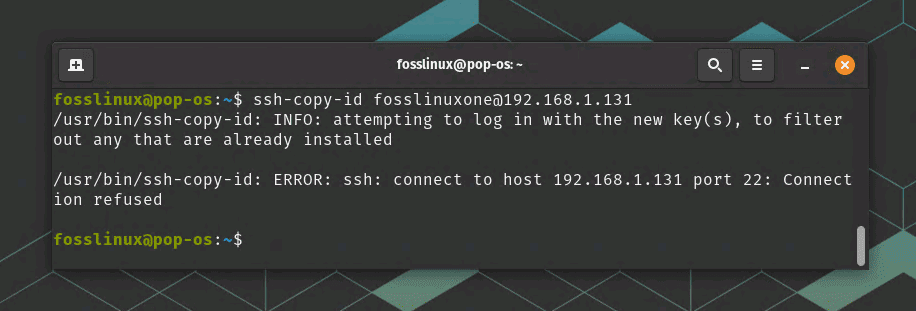
Copying the SSH key to server
Replace “username” with your username and “remote_host” with the IP address of your server. The system will then ask for your user password. Once entered, it will append the keys to the ~/.ssh/authorized_keys file in your user’s home directory.
Step 3: Log in using your SSH keys
Now, let’s see if we can log into the server without a password:
ssh username@remote_host
If you’ve followed the steps correctly, you’ll be logged into the server without being asked for a password! This moment was nothing short of magic for me when I first experienced it.
Common troubleshooting tips
Setting up SSH keys can be a breeze, but like with anything tech-related, things can sometimes go wrong. Here are some common issues:
Permission issues: If the SSH server has overly permissive rights over certain files and directories, it might refuse the key. So ensure that the ~/.ssh directory has 700 (drwx——) permissions, and the ~/.ssh/authorized_keys file has 600 (-rw——-) permissions.
Public key not found: If you’re trying to log in but the server isn’t accepting your key, double-check the public key on the server. Use cat ~/.ssh/id_rsa.pub to display your public key, and make sure it matches the one on the server.
Wrong passphrase: If you’ve set a passphrase and forgot it, you’d have to generate a new set of keys. It’s an annoying mistake, and trust me, I’ve been there.
Are there any alternatives to SSH?
Yes, there are several alternatives to SSH, although it is important to note that SSH is widely used and is the standard for secure remote administration of Unix-like systems. Still, here are a few alternatives:
Telnet: This is the “original” way of connecting to remote servers. However, it is insecure because it sends data, including passwords, in plain text over the network. It’s generally not recommended for use unless the network is secure and isolated.
rlogin and rsh: These are older Unix tools that function similarly to Telnet and SSH, but they suffer from the same security issues as Telnet, as they don’t encrypt the session.
Mosh (Mobile Shell): Mosh is a remote terminal application that supports intermittent connectivity, allows roaming, and provides speculative local echo and line editing of user keystrokes. It can be a good alternative to SSH, especially for mobile users.
Remote Desktop Tools (RDP, VNC): If you need a GUI, tools like RDP (for Windows servers) or VNC can be used. These aren’t exactly alternatives to SSH since they serve a slightly different purpose, but they can be used for remote access.
Secure Socket Funneling (SSF): SSF is a network tool and toolkit. It provides functionalities similar to SSH (such as remote procedure call and port forwarding) and some additional features like VPN.
PowerShell Remoting: For Windows environments, PowerShell Remoting might be a good alternative, allowing you to run PowerShell commands on remote computers.
Remember, though, that alternatives aren’t always better. SSH remains the trusted standard for remote server administration due to its security features, ease of use, and wide platform support. While it’s good to know there are other options out there, SSH is still the go-to tool for most sysadmins.
The pros and cons of SSH
Like all tools and technologies, SSH has its pros and cons. By understanding these, you’ll be better equipped to decide when and where to use it effectively. Let’s delve in.
The pros of SSH
- Security: This is perhaps the biggest advantage of SSH. It uses strong cryptographic techniques to ensure all communication between devices is encrypted. This prevents sensitive information from being intercepted or tampered with during transit.
- Wide Adoption and Support: SSH is supported almost universally across Unix and Unix-like systems. It has been the de facto standard for secure remote administration for years. You’ll also find excellent support in many other platforms and operating systems, including Windows.
- Functionality: SSH isn’t just about logging into a remote machine. It offers a wide array of features, such as file transfers (using SCP or SFTP), port forwarding (for securing non-SSH traffic), and the ability to mount remote directories on your local system using SSHFS.
- Passwordless Logins: Through the use of public and private keys, SSH can provide a convenient, passwordless login. Not only is this more secure than a password, but it can also simplify automated tasks.
The cons of SSH
- Complexity: SSH can be complex, particularly for beginners. Setting up public and private keys, managing SSH configuration files, and troubleshooting connection issues all require a learning curve.
- Security Misconfigurations: Although SSH itself is secure, it’s only as strong as its weakest link. Misconfigurations, like allowing root logins or using weak passwords, can compromise SSH’s security.
- Potential for Key Mismanagement: SSH key pairs need to be managed properly. If the private key is lost, you’ll lose access. If it’s stolen or inadvertently shared, your system’s security could be compromised. Key management is a critical aspect of SSH that should not be taken lightly.
- No Built-in Two-Factor Authentication (2FA): SSH does not natively support 2FA, a method of authentication that requires two types of identification. However, this can be mitigated with additional tools or PAM (Pluggable Authentication Modules) configuration.
While SSH has its downsides, its benefits — particularly its strong security and wide range of features — make it a crucial tool for anyone needing secure, remote access to Unix-like systems. It’s like a Swiss Army knife for remote computing; even with its drawbacks, it’s still an incredibly useful tool to have in your toolbox.
Wrapping up
The journey of setting up SSH keys on Ubuntu can be a fun ride, even with a few bumps along the way. These keys have become one of my most cherished Ubuntu features, despite my initial skepticism.
Remember, SSH keys are not just about convenience, they’re also about enhancing security. So, no matter how much you love your passwords (like me), do give SSH keys a chance!
Finally, I always encourage questions and discussion. If you have any issues, drop a comment. We learn from each other in the Linux world – it’s part of what makes it so unique and enjoyable!