There is an ample number of ways to check for any open ports on a remote Linux PC. Knowing open ports on a Linux machine helps system administrators to connect to the remote PC for troubleshooting system and cloud server issues.
TCP and UDP ports
TCP stands for Transmission Control Protocol. In this method, the computers get connected directly until the data transfer is taking place. Therefore, with this method, the data transfer is guaranteed and is reliable but puts a higher load on the server as it has to monitor the connection and the data transfer too.
UDP stands for User Datagram Protocol. Using this method, the data is sent in the form of little packages into the network with the hope that it reaches the final destination. It means the two computers are not connected directly to each other. This method does not provide any guarantee that the data you send will ever reach its destination. Load on the server is less, and so this method is used commonly by the system administrators first to try something that’s not so important.
Now that you know the types are ports on a Linux system, let’s get started with ways of finding the ones that are open.
Best ways to check if a Port is open on a Linux PC
There are multiple ways you can do it. However, the most reliable way to do this is by using the following commands:
- nc: netcat command
- nmap: network mapper tool
- telnet: telnet command
- echo > /dev/tcp/..
- netstat – tuplen
Let’s go through each method one by one.
1. netcat command
netcat is a simple Unix utility that can be used to write and read data using UDP and TCP protocol across network connections.
The primary reason for its design is to provide a back-end tool that works with the scripts and programs. It is also an exploration and network debugging tool that offers tons of features.
To use it, you need to install it in your distro using the respective installation commands.
For Ubuntu/Debian:
sudo apt-get install netcat
For Fedora 22+
dnf install nc
For RHEL/CentOS
yum install nc
By doing so, you can do the following operations with it.
- send UDP packets
- listen to arbitrary UDP and TCP ports
- Use IPv4 and IPv6 to do port scanning
Moreover, it also has three modes
The syntax of the command is as follows.
nc [-options] host-ip-adress port-number
Let’s try to use it on a remote computer.
$ nc -zvw10 192.168.0.1 22
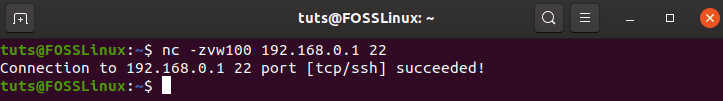
Showing nc command succeeding in connecting to an open port
As you can see, the connection succeeded. This means that port 22 is open. If the connection fails, then you will get an error message of “failed: Connection refused”
In the above command, we also used different options. Let’s list them below.
- z: zero-I/O mode which is used for scanning
- v: for verbose output
- w10: timeout wait seconds
2. nmap command
Nmap command is popular network security, auditing, and exploration command. Nmap stands for Network Mapper.
It also has a way to check for open ports. To do so, it utilizes a novel approach to using IP packets. It can also be used to learn about the services the host is providing. Other vital aspects that it can detect include operating system version, packet firewalls/filters, and so on! It is a useful tool.
Let’s see the nmap syntax below.
nmap [-options] [IP or Hostname] [-p] [PortNumber]
As you can see, its syntax matches that of the nc command. Let’s run it to get a better understanding.
nmap 192.168.0.1 -p 22
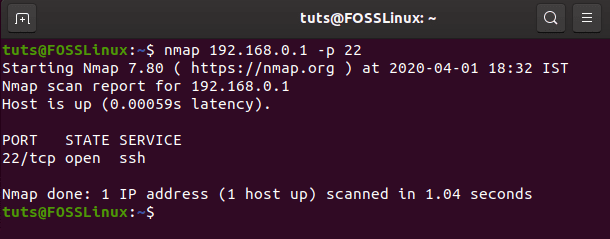
Running nmap command to check open port
If the port is closed, then it will show status is closed.
$ nmap 192.168.0.2 -p 103
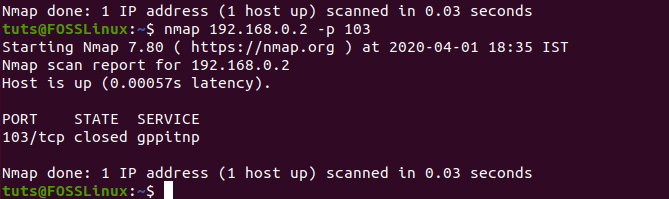
nmap command shows closed status for 103 port on 192.168.0.2
3. telnet command
The next command that we will go through is the telnet command. It is an old interactive communication command.
It is specially created for the remote computer interaction, and that’s why we are going to use it to check for open ports on a remote computer. The command is available on both Windows and Linux systems, but on a Windows system, it needs to be enabled before use. It runs over a TCP/IP network. Also, it connects over a remote computer or network equipment over port 23.
One more thing that you need to know is that it is not a secure protocol and must be used with SSH if you want to be encrypted and secure.
To install telnet in RHEL 7 or CentOS 7, you need to use the following command.
# yum install telnet telnet-server -yFor Ubuntu, use the following command
$ sudo apt install telnetd -yThe syntax of the command is as below.
$ telnet [IP or Hostname] [PortNumber]
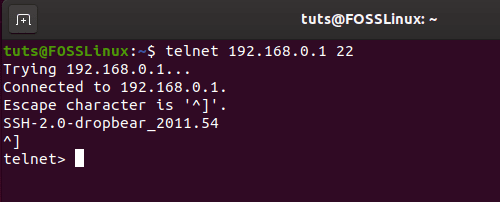
Shows telnet command in action with a successful connection
If the connection fails, then the port is not open, and you will get the following output.
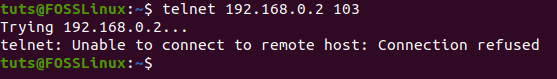
Shows connection refused using the telnet command
4. echo > /dev/tcp/…
There is another way to check for open ports. In Linux, everything is a file, including the host status and its port availability. This can come handy in cases where no commands are working on the remote host.
The syntax of the command is as below
echo > /dev/tcp/[host]/[port] && echo "Port is open"
or
echo > /dev/udp/[host]/[port] && echo "Port is open"
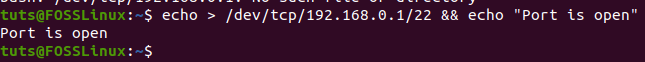
Port is “open” output
5. netstat -tuplen
The last command that we are going to discuss is the netstat command. It is a network utility TCP/IP command. It is used to print connections, interface statistics, multicast membership, and other network-related tasks.
The syntax of the command is as below.
netstat -tuplen
It will output the whole list of the IP addresses. The entries that have “Listen” in the “State” column are the open ports.
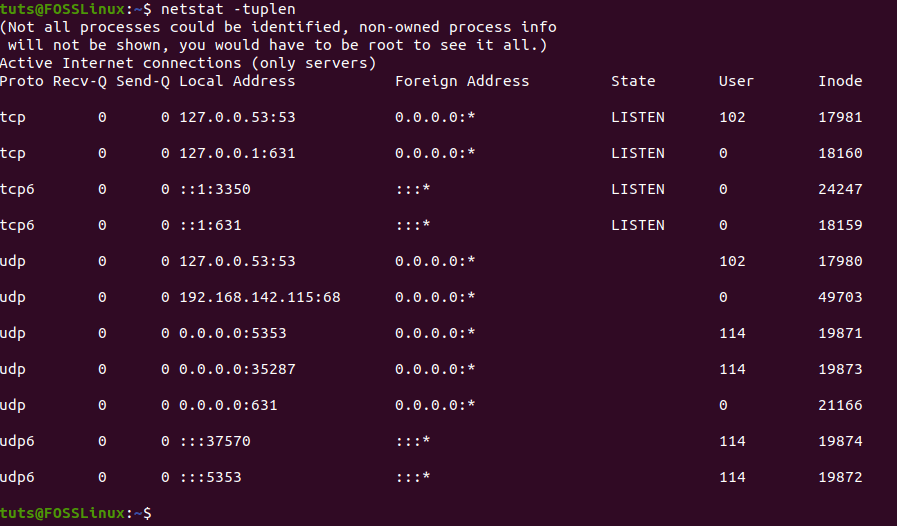
Shows the output of netstat-tuplen
Conclusion
This leads us to the end of our five ways to check if a Port is open on a remote Linux PC. So, which way are you going to use to connect to your remote Linux PC? Comment below and let us know.


3 comments
This tool seems useless, it says connection succeeded no matter what port I make up. nc -zvw10 HOST PORT. If I point it at any host thats online, no matter what port I make up it says the connection was successful. Its garbage to actually use for meaningful information in a real world situation as one used telnet to simply see if a port was actually open. Now I’m sure so-called network engineers will endlessly debate what “open” means, blah blah blah, we just want to see if a port is open…
Hello!
It worked fine for me:
nc -zvw10 172.217.3.132 80
mia09s19-in-f4.1e100.net [172.217.3.132] 80 (http) open
nc -zvw10 172.217.3.132 443
mia09s19-in-f4.1e100.net [172.217.3.132] 443 (https) open
nc -zvw10 172.217.3.132 21
yyz08s13-in-f132.1e100.net [172.217.3.132] 21 (ftp) : Connection timed out
netstat -tuplen —is it work remote