Most of the popular Linux distro includes extra files such as checksums and signatures when you download their ISO files. These are often ignored during download. While this is not a problem for the majority of users, some users typically those having an unreliable and slow internet connection, may run into a corrupted download.
Making use of the corrupted ISO images for installation can cause an unstable PC or in worst cases, an inoperable PC too. Hence, I suggest to first authenticate the ISO image before installing it.
Lately, in 2007, the Linux Minit official website was hacked. The hackers placed a modified ISO, which included a backdoor malicious file. Thankfully, the issue was solved quickly, but this shows us the importance of verifying the downloaded ISO files before installing them. Hence this tutorial.
Verifying Linux ISO checksum
Before starting our installation, you need to make sure that your Ubuntu system is up-to-date by using the following two commands:
sudo apt update sudo apt upgrade
Step 1. By default, the Coreutils and GnuPG packages are pre-installed on Ubuntu. So we need to make sure that both md5sum and gpg are working correctly.
md5sum --version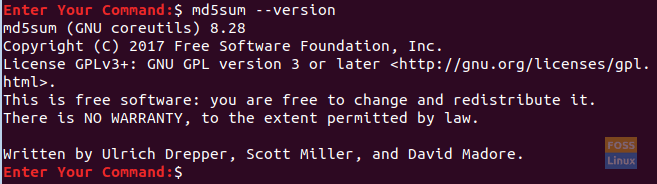
Md5sum Version On Ubuntu
gpg --version
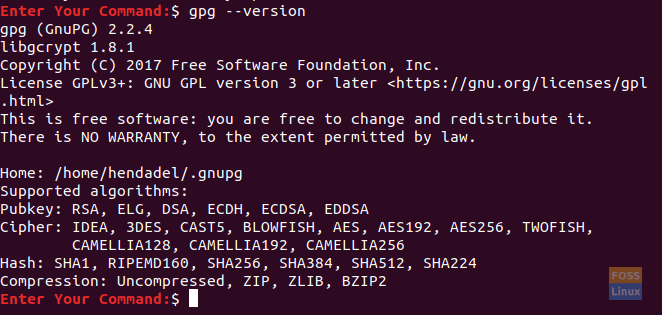
Gpg Version On Ubuntu
Step 2. Next, we need to download “SHA256SUMS” and “SHA256SUMS.gpg”, both files can be found alongside the original ISO files from the official Ubuntu website.
Go to the Ubuntu official website (Click here!!).
Ubuntu Official Website
Now search for the ISO you need to download, then you will find the previous files too, as you can see in the below screenshot.
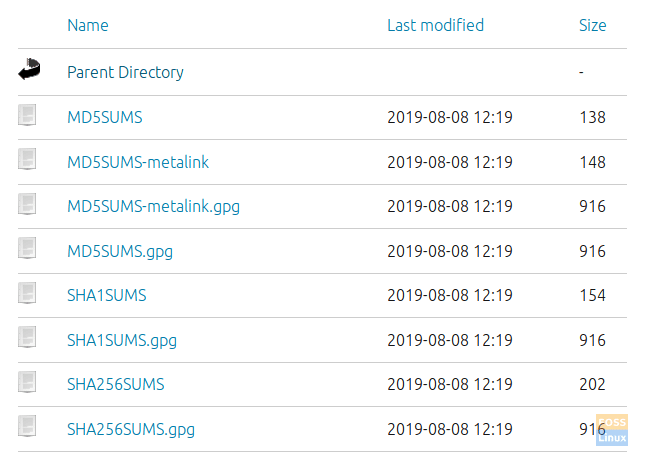
Select Check-sums File
Note: Press the file to download it, or you can easily right-click on it and choose to save link as. Please DO NOT copy the file content into a text file and use it because that will not work correctly.
Step 3. Now we need to check if we will need to get a public key or not. So we will run the next command to find out.
gpg --keyid-format long --verify SHA256SUMS.gpg SHA256SUMS
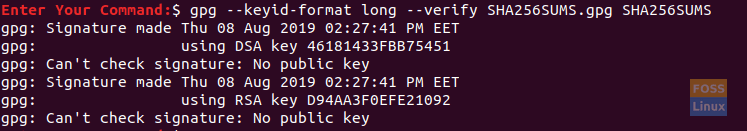
Check Public Key For Ubuntu Already Present
As you can see in the above screenshot, there is no public key found. Also, this output message tells you the keys used to generate the signature file. The keys are (46181433FBB75451 and D94AA3F0EFE21092).
Step 4. To get the public keys, you can use the next command along with the previous keys.
gpg --keyid-format long --keyserver hkp://keyserver.ubuntu.com --recv-keys 0x46181433FBB75451 0xD94AA3F0EFE21092

Public Key Retrieved
Step 5. Check the key fingerprints by using the next command.
gpg --keyid-format long --list-keys --with-fingerprint 0x46181433FBB75451 0xD94AA3F0EFE21092

Request ID From The Ubuntu Key Server.
Step 6. Now you can verify the checksum file again.
gpg --keyid-format long --verify SHA256SUMS.gpg SHA256SUMS
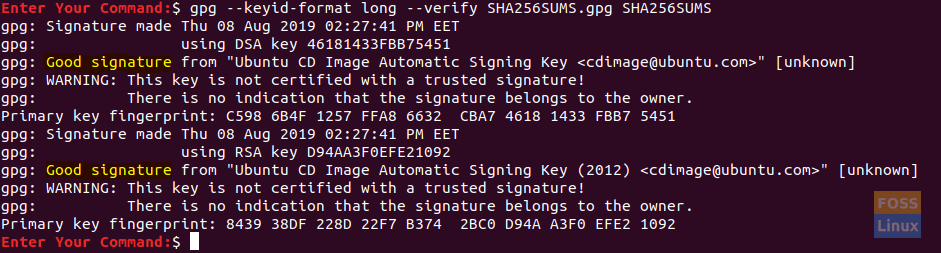
Verify The Checksum File Using The Signature
As you can see in the above screenshot, a good signature means that the files that were checked were for sure signed by the owner of the obtained key file. If a lousy signature was detected, then this means that the files did not match, and the signature is a bad one.
Step 7. Now let’s check the generated sha256 checksum for the downloaded ISO and compare it with the downloaded one in the SHA256SUM file.
sha256sum -c SHA256SUMS 2>&1 | grep OK
The output should look like the below screenshot:
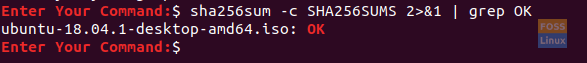
Check The Ubuntu ISO
As you can see, this means that your ISO matches the checksum file. Now you can proceed and use the downloaded ISO safely with no fear that it has been altered or downloaded incorrectly.

