Proxies are placed between various connections online. Because of the variations in the dimensions of the different connections, different types of proxies exist. While some proxies indicate a direct relationship between the proxy server and the client, some tell you which of the gadgets the proxy server is. In some cases, it can even show data management or how to deal with privacy in such a scenario. Depending on the proxy position, it can either be a forward proxy or a reverse proxy.
A point to note is that a forward proxy is different from a reverse proxy. As a result, this makes direct comparison complicated.
Forward Proxy
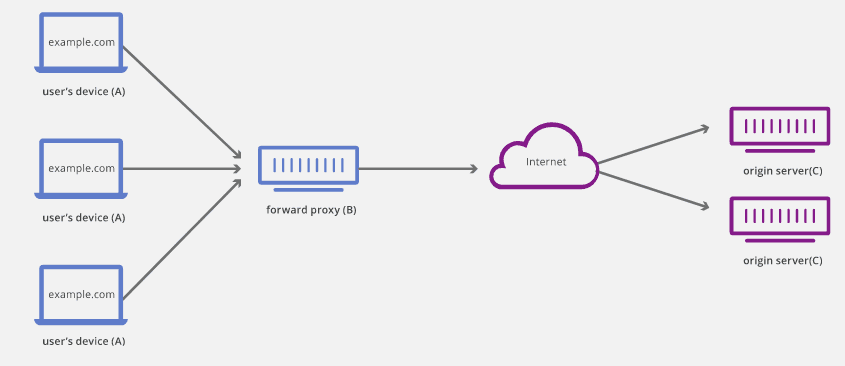
Forward Proxy
A forward proxy is applicable when you intend to bypass a network block. By default, people refer to it as a proxy. It works by receiving a request from a connection then subsequently fetching the needed data from the net. Users with clients connected with a firewall restriction will find forward proxy essential to access the internet. Essentially, what you are doing is foregoing the block by connecting to the proxy, which will get the necessary information from the intended service.
A forward proxy can maintain a record of requests, sources, the desired destinations, and the final responses. Doing so can receive many requests from different applications or clients and act as an intermediate between all of them. It can then determine which requests need to be allowed and those that should be denied. Requests that are permitted will then go through another security check by being forwarded to the firewall. Being the single point of entry makes a forward proxy strategically ideal for implementing policies on security. More so, if coupled with a firewall. The duo will form an impenetrable security wall to guard the internal network security.
This proxy type is vital and essential for most huge organizations and enterprise settings. It helps the organization accomplish various tasks that include tracking its employees’ activity online. Further, it allows the management to control employees from visiting certain websites, for instance, social media. It is also essential to guard the servers against attacks by malicious individuals within or outside the institution.
The other advanced versions of a forward proxy include an anonymous forward proxy responsible for denying target connections from accessing the client’s original IP address. Those have an anonymous connection.
Benefits of a Forward Proxy
A forward proxy connects to the end server, thus changing the client’s original IP address. By so doing, the client’s location and actual identity are hidden.
Forward proxies also help avoid regional restrictions like what is experienced when blocked from accessing connections in another country. A particular case at hand is the great firewall of China. The proxy gives a private connection to the initially restricted contents without a proxy.
Reverse Proxy
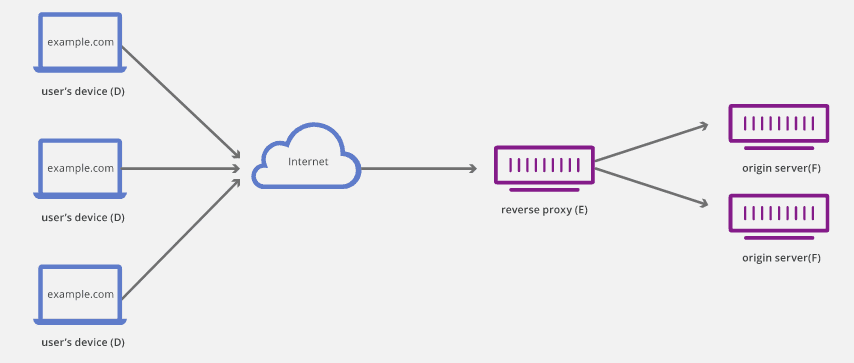
Reverse Proxy
Considering that an organization’s internal network has computers for clients, there is a need for extended protection other than solely relying on forward proxies. An ideal case scenario is when some resources need to be accessed outside the office. In such a case, guard the organization’s servers, and nothing does it better than a reverse proxy. So, what is a reverse proxy, and what roles does it play?
A reverse proxy is responsible for various tasks, including caching, data decryption, and authentication. In the past, some users and sites have even made claims that a reverse proxy was used for load balancing. However, this is not the core intention of reverse proxies. As a result, reverse proxies find suitable application in limiting accessibility to servers placed on private networks.
It is vital to note that reverse proxies do not provide clients anonymity. Instead, they provide anonymity for back-end servers. You ask why? It is almost obvious that it is not of value for the company to mask its clients’ exact location. However, they must do so for their servers. It is of the utmost importance when the company has an extensive number of servers. Reverse proxy comes in handy because it is essential to help control traffic to avoid overloading the servers. Besides, this proxy brings more than two servers to the same URL space.
Reverse proxies can be set up to work alongside a firewall. You can configure it to work alongside one, two, or more firewalls to protect your internal servers through filtering requests at different levels of access.
Both proxies have a lot of similarities in the way they function. The differentiating factor is reverse proxy has its client requests originating from the internet, whereas the forward proxies have an internal network behind them.
There are numerous benefits of using a reverse proxy irrespective of the number of servers you have. First, clients can only access your network via a proxy; thus, it becomes an extra huddle for attacks that could be malicious to your system. In short, a reverse proxy builds up a security wall for your site. Secondly, reverse proxies are known to enhance the speed of your site. It does so via caching. As a result, it is easier for pages that had been loaded initially to be accessed by users. This happens at the front-end part of development. In fact, it helps hide the downfalls of a back-end service that is not optimal in performance.
There is a specific type of reverse proxy called a backconnect proxy server that only gives a single connection to a rotating proxy pool. It is responsible for providing accessibility to the entire proxy pool. This way, there is no further need for proxy lists. They are no longer necessary. In fact, they become obsolete since the backconnect proxy server can handle this internally.
How Do Content Delivery Networks Use Reverse Proxy
Content delivery networks use a reverse proxy for both outgoing and incoming traffic for various reasons. They include the following:
The reverse proxy is strategically positioned to intercept traffic from the client before it is directed to the back-end servers. This has the benefit of mitigating against DDoS attacks. By distributing traffic hitting the system through the reverse proxy, the impact of a DDoS attack is greatly minimized.
It is also ideal for securing web applications. The latter approach is responsive in identifying malicious packets, for instance, requests from a hacker or bad bots. Thus, placing a firewall for your web app within a reverse proxy server is a practice extensively advocated by security and web specialists.
Whenever an application server has more than one backend server, a reverse proxy distributes traffic and load. That ensures that the system performs optimally by being highly available, thus sustaining the user experience. Highly available is a concept referring to the reverse proxy’s action to redirect traffic in case of a failure at one point of the server or if one of the servers in the pool goes down. The reverse proxy will evaluate which of the running servers has fewer loads before directing traffic from the dead server. This ensures that the site is continuously available without the clients noticing a problem. Besides, it helps to maintain HTTP sessions at any given time.
The reverse proxy will terminate upon receiving an incoming connection, starts by terminating the connection. Subsequently, it engages the back-end server to reopen the link. It works so smoothly that users cannot tell that their requests’ resolution is made through the back-end IP. The above approach is essential when you want to evade attacks, especially the denial of service attacks. Attackers will find it challenging to access because the client’s IP address is masked.
So, because of the complexity and intensity of both the hardware and software needed to set up a reverse proxy for a company, most opt to use content delivery networks. The latter will enable you to get all the benefits you intend to convey by setting up your reverse proxy. Sign up, and you have all the benefits. For example, Cloudflare is a CDN that provides the security details we have mentioned herein alongside other overall performance enhancements.
JSCAPE MFT Gateway
It is an example of a reverse proxy that is highly scalable and available. JSCAPE MFT Gateway finds application in internal network services for streaming purposes. It works by not storing critical content in a DMZ load balancer or operating through inbound ports. That means that users’ credentials will be kept and retained within the internal network.
As a software service, it has support for all notable platforms. These include Mac OS, UNIX, Linux, and Windows installers. It is also useful in ensuring government compliance on demands such as GLBA, PCI, and HIPAA. Further, it can facilitate support for virtually any protocol inclusive of MySQL, SFTP/SSH, SMTP, HTTP/HTTPS, and FTP/FTPS.
It has also been known to work effectively alongside the JSCAPE MFT Server in ensuring that clients have a solution that offers high levels of availability as far as file transfer is concerned. Besides, you can stream virtually from whichever network service is appealing to you.
Benefits of a Reverse Proxy
Revers proxy helps speed up your website’s loading speed by a large margin through caching at the front-end service.
It is also essential to hide your servers by placing them behind a firewall. Thus, the only option of accessing them is through a reverse proxy. I laugh it off, but clients will not see the reverse proxy any differently from the server.
Since a proxy lies between the back and front-end service, you can easily manage, control, and direct requests at the proxy level.
A reverse proxy is very useful in setting up SSL encryption. It decrypts the requests coming in then, in return, encrypts responses leaving. That will significantly free the source server from computations that would have been very expensive.
Also, note the invaluable role that a reverse proxy performs in ensuring that the server load is balanced.
Comparison of Forward and Reverse Proxy
Whereas a forward proxy is placed between itself and the desired server, a reverse proxy is put between itself and a client. That is almost directly opposite. In simple terms, that is like saying the forward proxy is at the end of the internet, whereas the reverse proxy connects to the server.
Besides performing varied and different duties, these proxies share the following:
– They can be a single point of connecting devices or servers
– They can block or give the authorization to access
– They act as a middle point in traffic for a client
Conclusion
This article delved into what a proxy is and highlighted the differences and applications of the two main types of proxies, namely reverse and forward proxy. We also looked at the benefits of both proxies.
Further, we elaborated on placing a reverse proxy if your main goal is to protect the servers. On the other hand, we cited why you need a forward proxy to protect clients.
Proxies need to be configured to work alongside a firewall. In fact, both reverse and a forward proxy can be set up to work with more than one firewall for enhanced security levels.
Overall, both proxies need to work in tandem for a practical and trusted security level to be attained by an organization that chooses to make it a priority.

