The Linux OS is famed for its awesome security system and protocols. This statement is the best-selling pitch that a Linux enthusiast will use to recruit a Linux newbie. No one wants to deal with a system prone to malicious attacks from unknown scripts or black hat hackers. Most of us can attest that we fell in love with Linux because its system did not need an antivirus. We did not need to scan every external device that made its way into our Linux system through the machine ports.
However, the functional attributes and security infrastructure of the Linux OS make it perfect in our eyes but not in a network-centered infrastructure. Our Linux systems’ security in a domain that connects thousands of computers is not guaranteed the same way it is on a desktop computer or laptop that connects to the internet or any other network once in a while. Moreover, the activeness of these desktop computers and laptops with Linux systems might prompt a user to consider malware and rootkit scanners’ implementation to be safe from the assumption of total guaranteed security. However, this article is here to consider a solution to the network-based threats that might face our systems.
When we think of a network-based threat, the first defensive instinct prompts us to consider a firewall. So, we need to learn everything about firewalls and then list some considerations that will work best for our systems against network-based exploits or attacks. Since we know that a Linux system is outstanding on its own, imagine the security authenticity of a Linux system that adds an extra layer of security to itself after already declaring itself as secure. To save ourselves from the confusion of this Linux juggle, we first need to define a firewall.
Consider yourself a network admin and your primary focus is on monitoring the behavior and performance of a system assigned to you. You will be dealing with the analysis of incoming and outgoing network traffic and also make some decisions regarding the security protocols that need implementation. However, you cannot perform all these tasks independently; unless you have a jinni hostage that grants you infinite wishes. You need the help of something superior, like a firewall.
It is a network security device that automates critical decisions based on incoming or outgoing network traffic. It will analyze network traffic and decide whether it is safe or unsafe. Unsafe traffic gets blocked while the safe traffic gets a green light into the network. A firewall references some pre-defined security rules that tag the analyzed network traffics as safe or unsafe.
Firewalls are not a new thing that started trending recently, their impact and contribution to network security have been felt for over 25 years now, and it continues to grow. You can think of them as the guardians of an internally defined network. They act as the network traffic bridge between a secured network and a controlled network and decide which traffic to trust and dismiss. A firewall can take the form of software, hardware, or a fusion of both.
A Firewall’s Objective
Since we know that a firewall is a defined guardian to an existing network, it will deny or kill the connection to suspicious network traffic. Killing this unwanted connection increases the network’s performance since the traffic from a legitimate connection will simultaneously increase. Therefore, an ideal network infrastructure should have computers, servers, and firewalls as part of the basic network components.
A firewall’s role as a component of this network infrastructure exists between the computers and the servers. Since they will now control the network traffic access from computers to servers and vice versa, the legitimacy of a defined network data remains private and secure. Having a network entity that monitors and limits network traffic is an invaluable addition to a network infrastructure, which in the long run makes a network admin more proficient in their role.
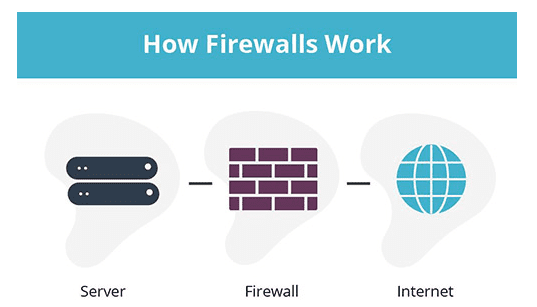
A network diagram with a firewall
A practical firewall-in-action example scenario is when dealing with a DoS (Denial of Service) network attack. In this case, rogue network traffic will target and flood your live website. The consequential objective of this network flood will be to overwhelm the web server hosting your site. If the webserver cannot handle the traffic pressure, it will either go down, or its functionality will collapse.
Hence, if you were running a hosted and growing online business and such a hiccup, you could lose significant clientele. Your business reputation will dwindle from negative customer reviews. However, if you did your firewall homework, you will protect yourself from this network vulnerability maze. A firewall will filter such traffic, find any hidden anomalies, and break the connection if needed.
How Firewalls Work
We now know that a firewall monitors the movement of data on an existing network and will reference existing pre-defined rules to block bad data and allow the passage of good data. However, the methodology behind how a firewall works is not direct but combines three approaches. They are Proxy Service, Packet Filtering, and Stateful Inspection.
Proxy Service
This firewall methodology prevents a network server from directly interacting with network traffic. The firewall places itself between the network server and the network traffic, assigning itself the intermediary role. Therefore, an end-user request made towards the server will first have to go through the firewall. The firewall then examines the end-user’s data packets on the network traffic and decides whether they are viable to reach the server based on its pre-defined network inspection rules.
Packet Filtering
This firewall methodology monitors the network connectivity facilitating the communication between a network computer or device and a network server. So, such a network is bound to have data packets that continuously travel through an existing network path. The network firewall will directly deal with these traveling data packets to filter out any intruders trying to access the network server. In this case, the firewall rules will use an access list that defines if the packet data should access the server. The firewall then counter-checks each transmitted packet data against this list and only allows passage to the viable ones.
Stateful Inspection
This firewall methodology works by analyzing an evident traffic flow pattern. It implements this analysis based on three parameters, namely state, port, and protocol. This firewall will either define a network activity as open or closed. Therefore, a continuous firewall monitoring activity will keep track of trusted and known data packets, and each time they re-emerge, they will be granted an authorized data passage. However, these data packets’ recurrence prompts their re-inspection for unauthorized data packets from malicious users or sources.
Types of Firewalls
Before we dive into the open-source firewalls to consider for your Linux system, it would be impolite not to mention the various types of firewalls that exist. The types of firewalls in existence directly correlate with the primary functionality they offer, as we are about to see.
Proxy Firewall
This firewall is a household name and was among the first to exist when the concept of firewalls started to attain the needed significance in a growing network-centered world. It is a gateway that grants the connection or communication between one network and another. The objective of this communication or connection is to interact with a specific application. In addition to this authorization security, a proxy firewall also caters to content caching. Hence, the outside world will not connect directly to a specified server without passing through mandatory firewall security checks. Its support for network applications also impacts their throughput capabilities and the overall network performance.
Stateful Inspection Firewall
As mentioned earlier, this firewall will either permit or disallow traffic based on the parameters: state, port, and protocol. This firewall’s activeness starts when a network connection is active or open and halts when the connection closes or ends. This window allows filtering decisions to take place. The foundation of these decisions is based on context and network administrator-defined rules. The context rule enables the firewall to reference previous connections’ info and identify data packets linked to a similar connection.
UTM (Unified Threat management) Firewall
This firewall borrows a Stateful Inspection Firewall’s functional approach and loosely couples it with antivirus inspection and intrusion detection inspection. Moreover, it leaves an allowance for extra services, if required, to tighten the security grip of the network. It is an ideal firewall recommendation for users considering cloud management. A UTM operates under the principle of ease-of-use and simplicity.
NGFW (Next-Generation Firewall)
Network firewalls have also taken a leap of faith into evolution. Their functionality can no longer be limited to stateful inspection and data packet filtering. It is now evident that next-generation firewalls are on the rise, and companies are taking this approach to deal with application-layer attacks and advanced malware. A next-generation firewall has the following traits or attributes.
- Integrated intrusion prevention
- Intelligence techniques to adapt to evolving security threats
- Stateful inspection and other standardized firewall capabilities
- Ability to detect and quarantine risky apps though application control and awareness
- The use of future information feeds as part of the firewall’s feature upgrade.
These capabilities need to the standard for every modern company’s firewall.
Threat Focused NGFW
This firewall combines the functionalities of a traditional NGFW and couples them with advanced threat remediation and detection. This threat-focused firewall helps you achieve the following:
- Complete context-awareness. It will help you group your network assets based on the viable vulnerability levels.
- Prompt reaction to network attacks. Dynamic hardening of network defenses through set policies contributes to the buildup of intelligent security automation features viable for your network’s stability.
- Better detection of evasive or suspicious activities. This objective is achievable through endpoint and network event correlation.
- Significant reduction in the duration between network threat detection and cleanup. The firewall will continuously monitor and stay alert for suspicious network activities or behaviors even after the previous threat inspection and management success.
- Reduced network complexities to ease its administration. The unified policies in place should help you work with a firewall that is easy to manage and monitor when a quick decision needs to be made concerning a suspicious network threat.
Virtual Firewall
The deployment of this firewall in a public or private cloud gives it the identity of a virtual appliance. A public cloud can be Google, AWS, Oracle, and Azure, whereas a private cloud can be Microsoft Hyper-V, VMware ESXi, and KVM. The defined virtual appliance instance works across both virtual and physical networks and will help monitor and secure their related traffic. At one point in your pursuit of network firewalls practical knowledge, you will come across SDN (Software-Defined Networks). You will be able to understand the role of a virtual firewall in the implementation of their architecture.
Hardware Versus Software Firewall
Since we have already discussed that a firewall can be software, hardware, or a combination of both, the firewall solution you are after might lead you into a dilemma. You might not know whether you need a software firewall, a hardware firewall, or a combination of both. Whichever the case, it is better to have one of them set up on your system to be safe from network vulnerabilities. However, your decision on the firewall to use should be based on a complete understanding between a software and hardware firewall.
Hardware Firewall
This firewall is defined as a configurable physical device capable of monitoring infrastructure-based network traffic by allowing or denying data packets transmission based on specified network settings. Since a hardware firewall is a separate entity or component from your physical server, this server will reap high performance. Your network traffic will be 100% under your control. This firewall is easily configurable, and it just takes a single device for you to decide inbound or outbound network traffic. It also gives you granular control to RDP and SSH services. With a hardware firewall, you can easily and directly configure a Virtual Private Network connection. Your infrastructure will continue to be accessible under a stable internet connection.
Software Firewall
A firewall that is installable on a local computer is the starting definition of a software firewall. Its functional objective is straightforward and will either permit or deny traffic towards or away from your local computer. However, a pre-configured set of network traffic rules need to be in place for this firewall to be objective in its functionality. The implementation of a software firewall does not demand any physical setup. The network traffic analysis under this firewall is exceptional. A user can block malicious traffic based on keywords.
The viability of having such a local firewall makes its traffic analysis routine efficient with security alerts. However, the implementation of a software firewall has one specific demand, all the devices on the network that want to benefit from it need to have it installed in their systems. Another notable concern is the compatibility between the software firewall and the network device’s operating system. Such an issue can weaken the effectiveness of your security infrastructure. The network device that hosts this firewall’s installation and configuration need to have capable hardware since this software is resource-intensive and might slow down a weaker machine’s performance.
Conclusion
Now that you know in-depth about what a Linux Firewall is, how it works, and what it can do for you, you may want to take a look at some of the best open-source firewalls for your needs.