You might ask, what is the necessity of a password manager? To answer this question, we have to breakdown the attributes of a good and secure password. These attributes are not related to the password we compose at a moment’s notice. You do not need a password manager or a password wallet for passwords related to your pet’s name, dream city to visit, or even your favorite pronounceable noun or verb.
While you have the right to use these kinds of passwords, we cannot confidently characterize them as secure under the Linux domain. Secure passwords are not easy to memorize, and that is why you need a password manager. First, let us consider the rules of a secure password.
Rules and guidelines for creating a secure password
If you do not want your user and system passwords to be victims of Brute Force Attacks, Dictionary Attacks, or Phishing Attacks, then you should consider the prowess of the Linux password generation tools at your disposal. These Linux tools produce passwords that adhere to the following traits.
- The generated passwords have a standard length. The length of the passwords you create should be between 14 and 15 characters long. Such a password length is not easy to decipher.
- The generated passwords are composed of a mixture of characters. You cannot use letters only to represent your passwords. It is the first trait of a weak password, especially when you want to use it on a high-end platform like your financial service app or cloud server. This password should blend with characters like symbols, numbers, Upper Case, and Lower Case numbers. This technique makes the password potent enough and won’t be affected by Brute Force or Dictionary Attacks.
- The generated passwords do not make use of common substitutions. A password like FOSSLINUX234 or FOSS234LINUX is a piece of cake to a Brute Force attacker. The use of random character replacement is the perfect fix for this issue.
- The generated passwords are not produced from memorable keyboard paths. Nowadays, we have keyboard recorders that are sufficient enough to record a user’s keyboard strokes. Using a keyboard path like qwerty is a bad implementation of a secure password because the Dictionary Attack algorithm will easily catch up on it.
Linux command-line based password managers
Now that you are familiar with the few important rules concerning the creation of secure passwords, it is time to learn the ropes on how to manage these generated passwords. You should not be using an excel sheet or a text editor to group and manage the awesome password strings you managed to generate. There is a cool way of achieving this objective. The Linux operating system offers support for command-line-based password managers.
These password managers store details like notes, titles, web URLs, and user credentials in an encrypted file format. Since the user and system passwords are classified as credentials, these Linux password managers are the perfect fit. These password managers create categorical and individual password files that a Linux system user can easily sort and identify.
Also, depending on the flexibility of the command-line-based Linux password managers we will review in this article, you might be able to use their platform to edit, add, generate, and easily retrieve your passwords. The shell scripts under these password managers are short and simple. They help temporarily place the user passwords on the system clipboard, which makes it easy to copy, paste, and track any changes linked to them.
Passmgr command-line based password manager
This password manager command-line utility has a simple and portable functional design. It favors the users of the RHEL-based Linux distributions like Fedora. You can use it to store your system or user passphrases and retrieve them through the Linux command-line interface. The default operation mode of Passmgr is as follows. It will first access the already generated and stored user passphrases.
Secondly, it flexibly permits the selection of these stored passphrases. Finally, the selected passphrases will be copied to the system’s clipboard. It is only for a limited duration so that the system user can paste the passphrase to a field (Web-based or Desktop) where it is needed. After this limited duration countdown expires, the system clipboard backtracks to its default state.
When you use Passmgr password manager, the encrypted file that contains your passphrase credentials will be accessible from Linux’s default Home directory. The encryption key responsible for the generation of this file is a derivative of Scrypt. The file encryption used is AES256-GCM.
The first step to installing Passmgr on your Linux system is first to fulfill two dependencies issues. You need to pre-install Go and the Xsel/Xclip command utility.
Go installation
Your Go download depends on the machine architecture; 64 bit or 32 bit, you are using. To be completely sure of the machine architecture hosting your Linux operating system, run the following command on your terminal.
# uname -m
An output like X86_64 implies that you have a 64-bit architecture machine or computer. Any other output other than this one is for the 32-bit architecture machine.
The first step towards Go installation is to update your Linux system.
# yum update
The next step is to download the Go package and extract it to the /usr/local/ directory.
# wget https://storage.googleapis.com/golang/go1.6.2.linux-amd64.tar.gz
# tar -xzvf go1.10.3.linux-amd64.tar.gz -C /usr/local/
Next, create a work folder which we will use to configure some system environment variables.
# cd /root
# mkdir go
# nano /etc/profile.d/goenv.sh
At the bottom of this file, add the following lines.
export GOROOT=/usr/local/go export GOPATH=$HOME/go export PATH=$PATH:$GOROOT/bin:$GOPATH/bin
Write Out (Ctrl+O) this file and execute it or make it active.
# source /etc/profile.d/goenv.sh
At this point, your Go installation is a success. You should check on the Go version that you have on your Linux OS by running the following command.
$ go version
Xsel/Xclip command installation
The final dependency before installing and configuring Passmgr is Xclip. Its installation is straightforward. On your RHEL-based Linux distribution, you first need to install several dependencies using the yum package manager. They are libX11.x86_64, libX11-devel.x86_64, libXmu.x86_64, and libXmu-devel.x86_64.
Next, download two rpm files related to our installation. Remember, these steps apply to the RHEL-based Linux distributions alone.
# wget http://dl.fedoraproject.org/pub/epel/7/x86_64/x/xsel-1.2.0-15.el7.x86_64.rpm
# rpm -Uvh xsel-1.2.0-15.el7.x86_64.rpm
# wget ftp://mirror.switch.ch/pool/4/mirror/epel/7/x86_64/x/xclip-0.12-5.el7.x86_64.rpm
# rpm -Uvh xclip-0.12-5.el7.x86_64.rpm
Passmgr installation
Now that we met the needed dependencies, installations setting up Passmgr should not be a problem. You only need one command string to access and enable Passmgr.
# go get github.com/urld/passmgr/cmd/passmgr
Now that you have the Passmgr tool downloaded on your Linux machine, you need to launch it and set a master password. This master password will be like the wallet key to accessing all the passphrases we will be securing through this tool. On your terminal, run the following command:
# passmgr
The terminal will respond with the following prompts:
[passmgr] new master passphrase for /root/.passmgr_store: [passmgr] retype master passphrase for /root/.passmgr_store: -- store is empty -- Choose a command [(S)elect/(f)ilter/(a)dd/(d)elete/(q)uit] a
From the above line prompt response, if we go with option (a) as depicted, we will be able to add a new passphrase and its associated user.
Enter the values for the new entry User: Brandon_Jones URL: fosslinux.com Passphrase: n) User URL 1) Brandon_Jones fosslinux.com
You can try using the other password management options (select, filter, and delete) available on Passmgr. If you need more options on using this password manager utility, run the help command on your terminal.
# passmgr --help
You will be able to interact with and use all the available Passmgr options.
Titan command-line based password manager
The next command-line-based password manager on our list is Titan. It, too, is a favorite password manager utility for RHEL-based Linux operating systems. Titan is flexibly extensible, and any Unix-like operating system can fully implement and use it. The encryption mechanism for the passphrases stored and accessed within Titan is employed from the OpenSSL library.
The specific encryption in use is AES. It implements 256-bit keys. Titan also goes an extra mile to protect its password database. The security of any password database is important to prevent other malicious users from compromising the integrity of the stored user credentials. For this reason, Titan uses keyed HMAC (Hash Message Authentication Code). The encryption process of the submitted user credentials also employs the use of a unique and cryptographic random initialization vector.
If you were wondering about the password database used by Titan, then it SQLite. Reason? It is straightforward, simple, and easy to deal with the SQLite database’s database schema.
Its installation on RHEL-based Linux distributions is as follows:
First, you need to install SQLite and OpenSSL.
# yum install sqlite-devel.x86_64 sqlite-tcl.x86_64
# yum install openssl-devel
# git clone https://github.com/nrosvall/titan.git
# cd titan/
# make
# make install
Now that we have a Titan password manager installed and correctly configured, we need a simple command-line walk-through on managing various user passwords. Since we installed SQLite, it makes sense that the first step should be the configuration of the main password database.
# titan --init /home/passwords/passwd.db
While this database is created, it is recommended that you also secure it with a password. Once done, populating the Titan database with user credential information is easy. You can employ the use of the argument options –add or -a.
# titan --add
Title: Contributor Username: Brandon_Jones Url: fosslinux.com Notes: FossLinux Account Credentials Password (Empty to generate new):
While adding other entries to the Titan database, you will need to decrypt them first. It helps visualize the entries you are making instead of blindly keying in data into the database. The following command is useful.
# titan --decrypt /home/passwords/passwd.db
You might also want to confirm the entries existing in the Titan database. Use the following command.
# titan --list-all
A sample output from using the above command should look like the following:
ID: 1 Title: Contributor User: Brandon_Jones Url: fosslinux.com Password: ************** Notes: FossLinux Account Credentials Modified: 2021-02-12 17:06:10
It would help if you remembered that we decrypted the Titan database to create a user credential sample entry. Now we need to return this database to its encrypted state as a tighter security measure. Execute the following command.
# titan --encrypt /home/passwords/passwd.db
There is more to using Titan password manager than through the few commands this article has expressed. If you need to exploit more Titan command options, use either of the following commands.
# man titan
or
# titan --help
Gopass command-line based password manager
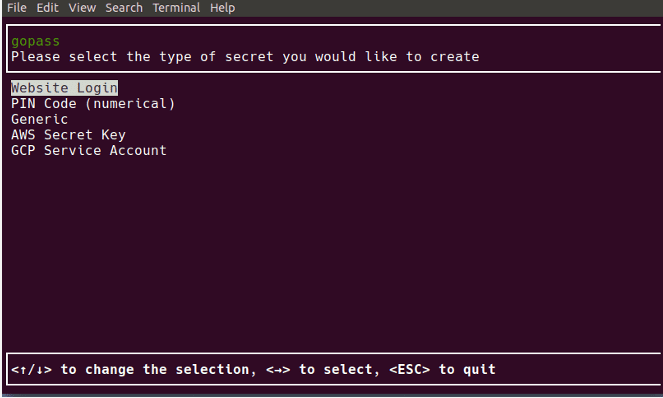
Gopass Command-Line Based Linux Password Manager
The default Gopass profile describes it as a team password manager. Regardless of this Gopass bio description, it is also useful as a personal password manager. Its creation is based on the go programming language. It would be best if you had Go installed on your Linux operating system to access and install Gopass. Go installation is detailed from its official site. Two viable installation options are available for all Linux users. You can access its installer for a guided installation, or you could compile it directly from the source.
If you already have Gopass installed and configured, you might need to access its updated features and upgrades. These updates and upgrades occur under the Gopass Github repository, where contributors and developers are actively making improvements. The following command helps keep your Gopass version updated.
$ go get -u github.com/gopasspw/gopass
This command is effective for the users that compiled it directly from the source. You need to be in the same directory as your previous Gopass version to execute this command.
This Linux password manager is described as easy, secure, and extensible. Its documentation also covers the usage of various Gopass commands to help improve your user experience. Its extensible nature is in its pursuit of an API integration that will help Gopass bond with other user binaries.
Kpcli command-line based password manager
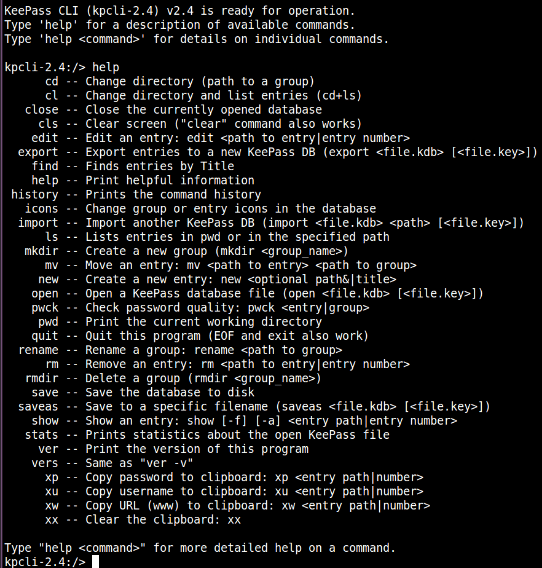
Kpcli Command-Line Based Linux Password Manager
While many users will choose to go with KeePassX or KeePass’s open-source nature as their ultimate password manages, Kpcli combines the features these two password managers have to offer and unravels them on your Linux command-line window.
Kpcli exists as a keyboard-driven shell. Its command-line interface allows you to add and edit personal and group passwords. Just think of all the things KeePassX and KeePass password managers can do graphically and then substitute them to the command-line interface of Kpcli. This terminal-based password manager also supports renaming and deleting of personal and group passwords through an admin user. It also uses a clipboard for holding copied usernames and passwords before using a target site’s or platform’s login form. To get rid of this data on the clipboard after it has been used, Kpcli has a command to empty it. Its official site has an update on its download and installation.
Pass command-line based password manager
Pass Command-Line Based Password Manager
This Linux password manager simplicity strictly adheres to the Linux philosophy. It uses a file encrypted under gpg for storing generated passwords. It encourages storing these password files with a filename similar to the platform or website linked with the stored user credentials. The storage of these encrypted files can adhere to flexible folder hierarchies. The generated and encrypted files are also transferable from one machine to another.
Pass creates a common storage path, ~/.password-store, for all your generated passwords. If you need to add, edit, generate or retrieve a password, you will use the pass command alongside its other supported command arguments. It also employs the use of your system’s clipboard to hold copied user credentials temporarily. It supports the use of git to track password changes.
To list stored passwords and other credentials under Pass, use the following command.
$ pass
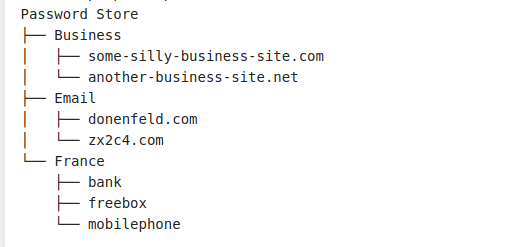
Using Pass Command-Line Based Linux Password Manager
Based on the above screenshot from its official site, we can also display a stored password based on the Email category.
$ pass Email/zx2c4.com
To copy the password associated with the above Email to a clipboard, you will run the following command.
$ pass -C Email/zx2c4.com
Other commands to play with are the insert, generate, and rm commands for adding passwords, generating passwords, and removing passwords, respectively.
More on its example usage can be found here.
The following are the installation steps for various Linux distributions.
Debian:
$ sudo apt install pass
RHEL:
$ sudo yum install pass
Arch:
$ pacman -S pass
Conclusion
Most of these listed Linux password managers are supported by other Linux distributions. The trick to getting them in your Linux machine is knowing how to adapt to their different package managers. There are other Linux-supported password managers to consider, like Ylva and Passhole, if you need a bit more flexibility from this brief list. This article has ensured that generating and managing secure Linux passwords is no longer an entity on your bucket list. Not only are you comfortable with the options of generating and managing your passwords, but you also understand the rules that make your generated passwords strong enough.
Since these Linux password managers are effective through the command-line interface, it is a great option for users that are familiar with SSH remote login. You do not have to be physically present in front of your machine to access the password files you need to use. This latter statement implies that you only need to memorize a master password that will help access and manage all the other stored systems and user passwords you will be using. With the Linux command-line-based password managers, your system and user credentials are in safe hands.

