A proxy service aims to act on behalf of another. It could be to act on behalf of another person or behalf of another client machine or server. Hence, when we talk proxy servers, we have forward proxy servers or reverse proxy servers.
A forward proxy server is positioned at the edge of your network to regulate outbound traffic according to preset rules in a shared network. It is also used to disguise a client’s machine IP address and block malicious inbound traffic. Forward proxy servers keep track of requests, responses, sources, and destinations, allowing different clients to send out various requests to other servers through the forward proxy, intermediate for all of them.
Self-Hosted Proxy Servers
A reverse proxy server proxies on behalf of servers and accepts requests from external clients on behalf of servers. Reverse proxy servers also act as load balancers which plays a critical role in providing high availability to your network services.
Proxy servers play a critical role as they can serve as a single point of access and control, making it easier for you to manage security policies for your network. Some people use self-hosted proxy servers to get past geographic restrictions, reduce bandwidth consumption. To improve response times through caching, restrict access to certain websites or IP addresses, eliminate some annoying ads, or protect children from Internet harm.
The article will highlight some self-hosted proxy servers available for your to install and use for your network.
1: Privoxy proxy

Privoxy Proxy
Privoxy is a non-caching web proxy build to enhance users’ privacy. It boasts enhanced filtering capabilities for modifying HTTP headers and web page data, controlling access, and removing super annoying ads. You can easily configure Privoxy, and it offers flexible configurations for multi-user networks and single-user systems.
You can configure Privoxy as an HTTP proxy or as an intercepting proxy if you combine it with a packet filter. You can easily configure and set up Privoxy in Firefox from the Manual Proxy Configuration menu under the Tools Settings. From the official Privoxy man page, you can only proxy HTTP and HTTPS traffic and a guideline not to use Privoxy with FTP or other protocols not officially listed.
Privoxy has been under release since 2001 under the GNU General Public License.
Privoxy is available for Linux, DD-WRT, OpenWrt, Windows, macOS, OS/2, BeOS, etc. Privoxy makes it into our list because it is relatively easy to install, configure and get running. The default configurations are sufficient for locally defined exceptions and locally defined filters. The concept of actions in Privoxy gives you, as the user, great control to manipulate data streams between remote sites and the browser. Some Privoxy actions available for you include blocking websites, managing cookies, URLs, or grouping URLs using regular expressions.
2: Swiperproxy
SwiperProxy is an open-source project written in Python. If you need a web proxy that gives you less hustle to configure and get running, SwiperProxy is your choice. SwiperProxy can be easily set up using 25 lines of well-documented configurations. Despite SwiperProxy being a minimalist web server, it is lightning fast and has features that support HTTP, HTTPS, logging, URL rewrites, and blocklists.
It works great with all major web servers, including Apache, Nginx, Varnish, and can be installed in all major distributions. It also allows you to place a reverse proxy in front of it, increasing security and giving you more configuration options.
It is an excellent place to learn to configure and set up self-hosted proxy web servers. SwiperProxy has a simple procedure to run it as a self-containing proxy or as a daemon.
Run Swiperproxy with the following terminal command:
$ sudo -u swiperproxy python Proxy.py -c proxy.conf
SwiperProxy is an open-source project hosted on GitHub and is available under the MIT license. Learn more on how to get started with SwiperProxy from their official quickstart GitHub page.
3: Squid Proxy Server

Squid Proxy
Squid is a free, open-source proxy server supporting various protocols such as HTTP, HTTPS, FTP, etc. It features a reverse proxy (HTTP-accelerator) which serves as a web cache daemon that caches incoming requests for outgoing data. It features several traffic optimization options, access control, authorization, logging facilities.
The other day, a colleague asked why I run Squid on my workstation. These are some of the points I highlighted to her.
There has been exponential growth in web content and the Internet, making a necessity for a caching mechanism a necessity. Squid has some powerful caching primitives which hint to servers and applications on how content should be cached, validated, and revalidated. Caching improves user response times and the amount of bandwidth required to serve the web content.
With Squid, you can quickly scale your web projects with its content accelerators. Thousands of websites use it to improve their content delivery.
Squid runs on all major Linux operating systems and Windows. Hundreds of ISPs worldwide use it to provide the best possible internet experience and save on bandwidth.
You can visit their official Squid homepage (They have a great logo!!) to learn more about the Squid project or contribute as a developer or user through their extensive support options like the Bugzilla database or mailing list.
4: Traefik Proxy
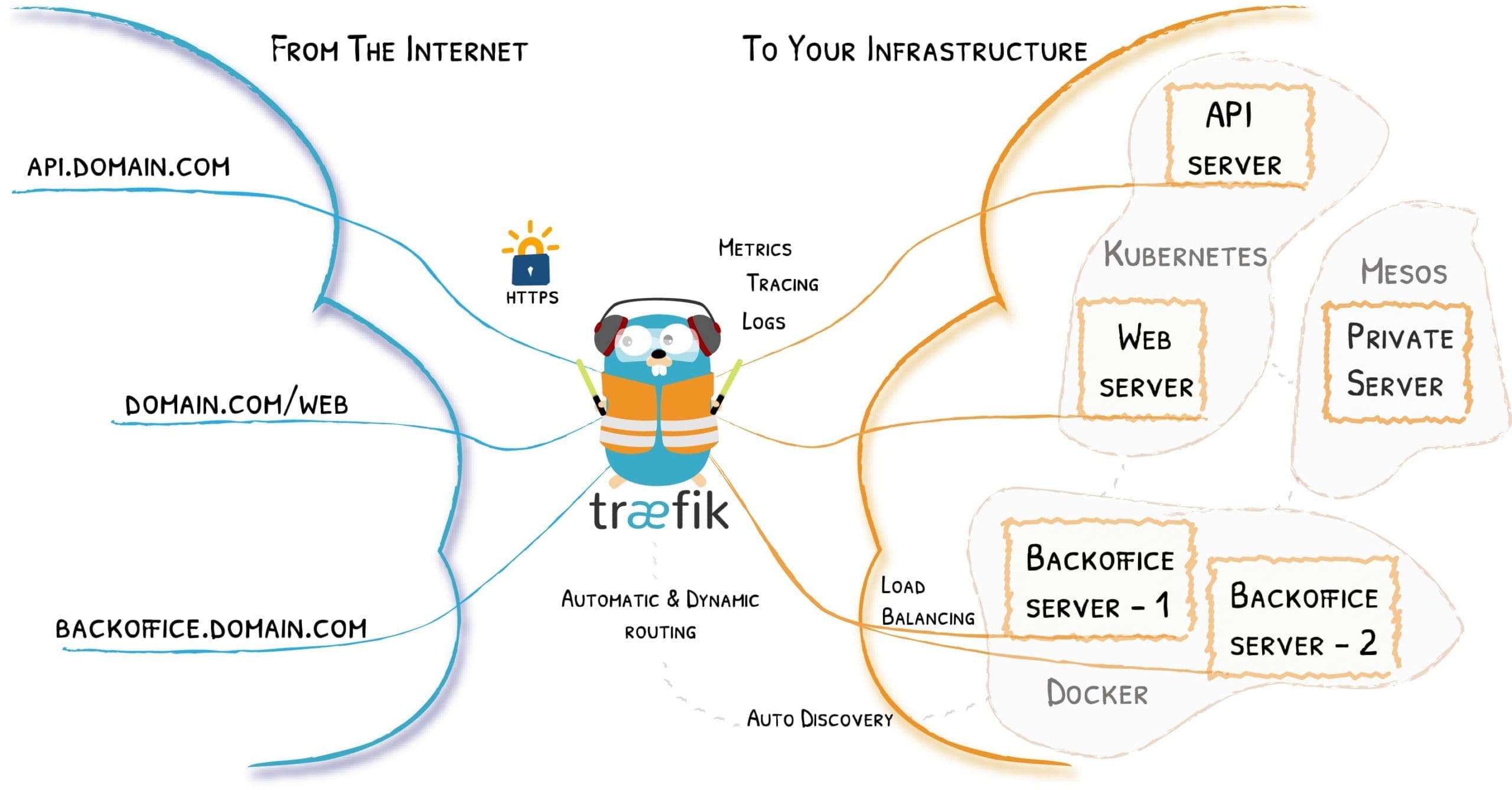
Traefik Infrastructure
Træfɪk is a modern, fast HTTP reverse proxy and load balancer that is optimized for deploying micro-services. It is an exciting open-source project written in the Go programming language. Træfɪk makes our list because it is easy to configure and is designed for modern cloud-based services. You can integrate it with other services like orchestration tools and service discovery mechanisms like Docker Swarm, Kubernetes, AWS, Rest API, Etcd, etc.
Træfɪk can be automatically and dynamically configured by any user and does not require any extensive knowledge of networking or proxy servers. Træfɪk can scan your infrastructure to discover the suitable configurations and services to serve requests in your infrastructure. Træfɪk can allow you to add, remove, kill, upgrade, or scale services with ease.
Other features supported by Træfɪk include WebSockets, HTTP/2, hot reloading, GRPC, and HTTPS using Let’s Encrypt certificates. It keeps access logs, and it is easy to configure metrics such as Datadogs, Prometheus, Rest, or InfluxDB.
Moreover, Træfɪk ships with a simplified HTML-based web-based user interface. Managing events couldn’t be any easier. Træfɪk is packaged as a single binary file and is available as a docker image. Learn more about the project from the Traefik Team, whose primary goal is to make a simple to use proxy/edge router.
5: Tinyproxy
Tinyproxy is a lightweight open-source HTTP/HTTPS proxy daemon for all major Linux and Unix operating systems. Tinyproxy is distributed under the GNU GPL license. Tinyproxy is designed to be a fast and yet small proxy that is ideal for use cases such as embedded deployments and small networks.
Some desirable features include the buffering connection concept, where Tinyproxy will buffer a high-speed response from a server and relay it to the client at the highest acceptable speed. It features an anonymous mode that allows individual HTTP headers to be allowed through or blocked from entering your infrastructure.
It supports HTTPS, URL-based filtering, access control using subnets and IP addresses, transparent proxying, and an extensive privacy feature. Its privacy feature allows you to restrict the data from an HTTP server to your web browser and what data is allowed from your web browser to the HTTP server. Tinyproxy has a security feature where it runs without any special privileges, which minimizes the chances of your infrastructure being compromised.
Moreover, as the name suggests, Tinyproxy has a small memory footprint of about 2MB with Glibc. The CPU load on your local machine increases linearly with the number of successful connections. In essence, with such a tiny memory footprint, Tinyproxy can run on old hardware without compromising on its performance. Explore more configuration options and features here.
6: HAProxy
HAProxy or High Availability Proxy is a free and open-source load balancer. It also functions as a reverse proxy for TCP and HTTP applications. HAProxy is a very fast, reliable proxy built for high availability.
HAProxy is a leading standard in load balancing, and you can use it to distribute workloads and improve the performance of applications and websites in your infrastructure. It has shown excellent results in minimizing response times and increase throughput.
Other outstanding features of HAProxy include services such as Layer 4 and 7 load balancing, support for HTTP, HTTP/2, gRPC, FastCGI, SSL/TLS terminator/initiator/offloader, a caching proxy, a traffic regulator, a content-based switch. It also protects against DDoS and service abuse. It implements stickiness (maintain a client on the same server across different events), content switching, HTTP rewriting and redirection, advanced health checking, logging, and statistics. Moreover, it features a CLI (command-line interface) for server management which comes in handy for users who prefer interacting through commands.
HAProxy
HAProxy is multithreading with an event-driven, non-blocking engine with a high-speed I/O layer. The priority-based multi-threaded scheduler enables it to handle tens of thousands of concurrent connections. It utilizes the PROXY protocol to pass the relevant client’s connection information to servers.
HAProxy has very impressive security records with very few vulnerabilities reported by users over the years of its existence. It limits attacks through features such as self-isolating using chroot, avoiding disk access after initialization, and dropping to a non-privileged user group on startup.
Users can define an access control list to allow access based on a client’s request and metadata. All these features combined with rate limiting, IP whitelisting, or blacklisting offer formidable security features for your infrastructure.
Some notable high-traffic users of HAProxy include GitHub and Twitter. You can find more features and add-ons on the HAProxy Enterprise commercial option available through HAProxy Technologies.
7: Pound proxy
Pound proxy is a lightweight open-source reverse proxy and load balancer that can also be deployed as a front-end for web servers. Pound makes our list partly because the HAProxy team recommends it as an alternative to HAProxy on the official HAProxy homepage.
Pound proxy is distributed under the GPL license. It was built to enable the distribution of workloads among several web servers and build a convenient SSL wrapper for web servers.
With Pound proxy, you get a reverse proxy, a load balancer that works while keeping session information, an SSL wrapper that decrypts HTTPS requests from browsers and passes them as plain HTTP back-end servers. It is an HTTP/HTTPS sanitizer that verifies requests for the correctness and is also a fail-over server that monitors running and failing servers to determine the best server to pass client requests.
Pound proxy is a minimalist program that can be easily audited for security problems. It can run as a setgid/setuid or in chroot without accessing your hard disk, thus posing no threat to your hardware. Pound proxy is not a web server or a web accelerator and therefore has no caching capabilities.
8: Skipper proxy

Skipper Proxy
Last but not least, we have a new kid on the block, Skipper. Not to be confused with the informal name for a captain in a team or a ship. Skipper is an open-source project to create a free HTTP router and reverse proxy for service composition. It has been designed to handle over 800k HTTP route definitions beyond what you would easily manage in Nginx or Apache. It is highly configurable and can be extended with custom filter logic, lookup, and configuration sources. But by default, Skipper comes with out-of-the-box configurations and a default executable command with a few built-in filters, which you can use on the go.
Its main features and some use cases include; a service to identify routes based on the requests path, host, method, or headers. It allows modification of clients’ requests and responses for each route. It can serve as a Kubernetes Ingress controller in a cloud infrastructure. Skipper can also update its routing rules from multiple data sources such as static files, etcd, Kubernetes Ingress, and custom sources without downtime.
Please find out more about Skipper’s features and integration with Kubernetes on the Skipper homepage or download the source code from its active Github page.
Your next step…
There are many solutions and services to choose from if you require either a forward proxy or reverse proxy in your infrastructure. There also many other wonderful services and solutions that can act as alternatives to proxy servers. I excluded seasoned players in the game like Nginx and Apache HTTP Server, popular HTTP servers that can be configured to act as reverse proxy servers.
Other options worth exploring are Pi-hole (for use with Raspberry Pi single-board computers), Varnish HTTP Cache, Pomerium, Microproxy, Redbird, etc. We could say, ‘Too many to mention.’
But to get started, you should learn to install a configure some popular self-hosted servers in a virtual environment. Proxy servers allow you greater control of your network and internet infrastructure.

2 comments
I just want to let you know that HAProxy is strictly a reverse-proxy. I’ve been trying to set it up for the past couple of weeks and in the end, I ended up with tinyproxy (quite good!) instead.
I can give you an example:
During execution, HAProxy will not resolve hostnames when working in “proxy mode”. Now tell me, what is the use of a forward proxy (in which this list is about) that only accepts ip addresses ?
Anyway, HAProxy is quite good, it just shouldn’t be on this list
Hi hydrocat,
It is considered good security practice to filter connections to the outside world. The easiest way to do this, especially with larger enterprises is through the use of a proxy server that forms the border between the internet and your local network. It would be the main egress and ingress point of your network for endpoints (clients and/or servers). It enables you to easily monitor the connection and control what type of connections are allowed or blocked.
At some stage it becomes inefficient to modify firewall rules everytime a server gets deployed that requires connection to the internet (i.e. for vendor updates), it becomes then easier to use a centrally accessible proxy server to facilitate that connection and apply filtering on that level.