FreeLAN is a PC software that implements peer-to-peer, a virtual private network(VPN), and full mesh methodologies to create secure site-to-site or point-to-point connections in bridged or routed configurations and remote configurations access facilities.
When it comes to encoding or encryption, FreeLAN utilizes the OpenSSL library to encrypt the control channels and the data. It allows OpenSSL to perform all the encoding and authentication work, permitting FreeLAN to use all the cyphers available in the OpenSSL package. FreeLAN incorporates a couple of ways to authenticate peers with each other. From version 2.0, FreeLAN provides pre-shared keys, usernames, and password-based and certificate-based authentication.
What do you do if you intend to use a VPN in a much more flexible way rather than the way VPN services offer it? Or using third-party servers not permitted or insufficient? What if you need to create a secure network? In such instances, FreeLAN can be the solution you have all been looking for.
In this guide, we will cover some essential features offered by FreeLAN, some of their pros and cons, describe the uniqueness of its configuration and use, how to set it up on our Linux machine, and finally give some recommendations.
FreeLAN is unique from other virtual private networks as there is no User Interface(UI). As such, you would not be able to use the OpenVPN client with this VPN, which is one of the key reasons why it is not recommended if you want to hide your IP or unblock sites. For such tasks, you can find other VPN applications configured with easy-to-use and more efficient functionalities. Let us now look at some of FreeLAN’s features.
FreeLAN features
- Allows you to mask your IP address.
- Unblocking websites
- Reliable traffic encryption
- Creating the peer-to-peer(client-client) tunnel
- Creating the client-server tunnel
- Creating a network that comprises several computers and servers in different combinations
- It uses 128/256-bit encryption
- It is supported by all major platforms(Windows, macOS, and Linux).
- It is entirely free.
FreeLAN pros
FreeLAN is free
The software is distributed according to the GNU GPL license, which means that it is a free, open-source one that allows modification, but you cannot develop a paid product on its base.
It is also convenient for generating your infrastructure based on FreeLAN tech.
Multiplatform
FreeLAN is a robust software compatible with OSX, Sailfishos, Linux Debian, Windows, and Docker.
Has high-security standards
FreeLAN gives AES-128-GCM and AES-256-GCM encryption standards with the RSA cryptosystem and SHA 256 algorithm. And as a matter of fact, AES-128 is now recognized as the official encryption standard for protecting the national data of the USA, and AES-256- is highly sensitive data.
The pros are pretty important. But it also has its cons, which we cover in the guide’s next section.
FreeLAN cons
It lacks a detailed documentation
At first glance, FreeLAN looks credible and more professional. It also seems right until you turn to technical instructions and details. There is limited information about the FreeLAN technology setup procedure’s opportunities and how to utilize it. There are no real-world examples of using it. Also, there are no specifications of the software configurations but only the links to the source code and technical specifications for the FSCP protocol.
Complicated and Unpredictable setup
The lack of structured and detailed data/information makes it challenging to test the opportunities of FreeLAN. Besides, the installer does not check the versions of GCC and Python installed. This raises unexpected errors that you cannot use to define the reason for the problem if you are not experienced enough.
For instance, you cannot set up FreeLAN 2.2 and 2.3 if Linux CentOS applies any Python version earlier than 2.7 and a g++ version earlier than 4.7. Furthermore, even after fixing all the discrepancies, you might find an unsuccessful installation.
Installing FreeLAN on Debian, Ubuntu, or their derivatives
First, we will initiate the installation process by updating our system’s cache repo. This can be attained by issuing the following command:
sudo apt update
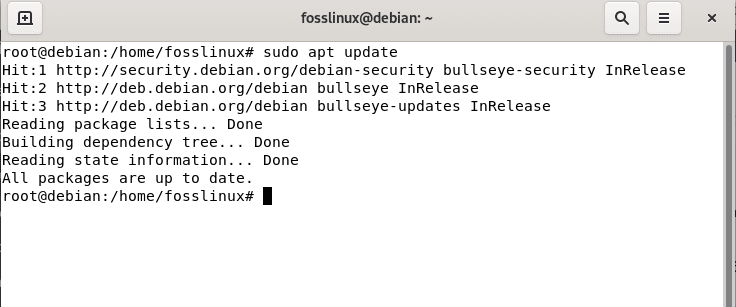
Update system cache
After that, you may or may not be alerted of the number of packages that need to be upgraded at the end of the update command. In case you have packages that need to be upgraded, then issue the following command:
sudo apt upgrade
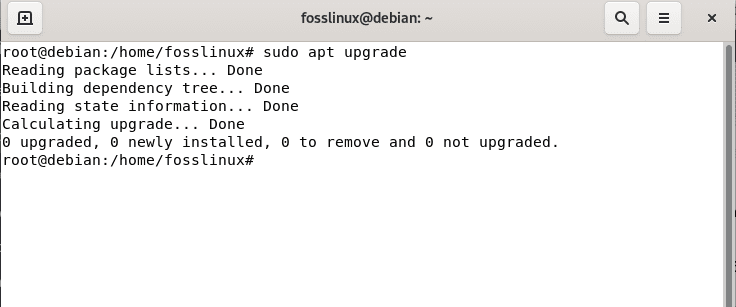
Upgrade system cache
Then finally, run the following command to set up Freelan on your Linux system:
sudo apt install freelan
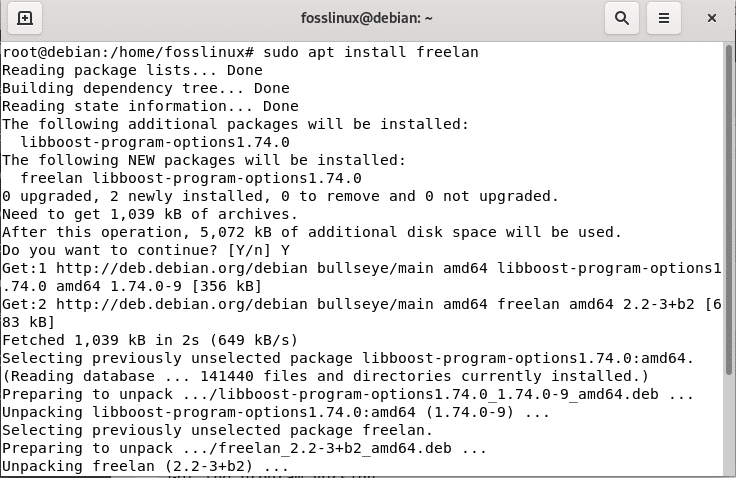
Install freelan
And that is it in the installation phase. However, FreeLAN, as earlier said, is a complicated setup application with no UI. We have compiled nearly all its functionalities to get you going with this software.
Here are the described FreeLAN functionalities:
Generic options: -h [ --help ] Produce help message. -v [ --version ] Get the program version. -d [ --debug ] Enables debug output. -t [ --threads ] arg (=0) The number of threads to use. -c [ --configuration_file ] arg The configuration file to use. Configuration: FreeLAN Server options: --server.enabled arg (=no) Whether to enable the server mechanism. --server.listen_on arg (=0.0.0.0:443) The endpoint to listen on. --server.protocol arg (=https) The protocol to use for clients to contact the server. --server.server_certificate_file arg (="") The server certificate file. --server.server_private_key_file arg (="") The server private key file. --server.certification_authority_certificate_file arg (="") The certification authority certificate file. --server.certification_authority_private_key_file arg (="") The certification authority private key file. --server.authentication_script arg (="") The authentication script to use. FreeLAN Client options: --client.enabled arg (=no) Whether to enable the client mechanism. --client.server_endpoint arg (=127.0.0.1:443) The endpoint to connect to. --client.protocol arg (=https) The protocol to use to contact the server. --client.disable_peer_verification arg (=no) Whether to disable peer verification. --client.disable_host_verification arg (=no) Whether to disable host verification. --client.username arg The client username. --client.password arg The client password. --client.public_endpoint arg A hostname or IP address to advertise. FreeLAN Secure Channel Protocol (FSCP) options: --fscp.hostname_resolution_protocol arg (=ipv4) The hostname resolution protocol to use. --fscp.listen_on arg (=0.0.0.0:12000) The endpoint to listen on. --fscp.listen_on_device arg The endpoint to listen on. --fscp.hello_timeout arg (=3000) The default timeout for HELLO messages, in milliseconds. --fscp.contact arg The address of an host to contact. --fscp.accept_contact_requests arg (=yes) Whether to accept CONTACT-REQUEST messages. --fscp.accept_contacts arg (=yes) Whether to accept CONTACT messages. --fscp.dynamic_contact_file arg The certificate of an host to dynamically contact. --fscp.never_contact arg A network address to avoid when dynamically contacting hosts. --fscp.cipher_suite_capability arg A cipher suite to allow. --fscp.elliptic_curve_capability arg A elliptic curve to allow. Security options: --security.passphrase arg A passphrase to generate the pre - shared key from. --security.passphrase_salt arg (=FreeLAN) The salt to use during the pre-shared key derivation. --security.passphrase_iterations_count arg (=2000) The number of iterations to use during the pre-shared key derivation. --security.signature_certificate_file arg The certificate file to use for signing. --security.signature_private_key_file arg The private key file to adopt for signing. --security.certificate_validation_method arg (=default) The certificate validation method. --security.certificate_validation_script arg (="") The certificate validation script to use. --security.authority_certificate_file arg An authority certificate file to use. --security.certificate_revocation_validation_method arg (=none) The certificate revocation validation method. --security.certificate_revocation_list_file arg A certificate revocation list file to use. Tap adapter options: --tap_adapter.type arg (=tap) The TAP adapter type. --tap_adapter.enabled arg (=yes) Whether to enable the tap adapter. --tap_adapter.name arg The name of the tap adapter to use or create. --tap_adapter.mtu arg (=auto) The MTU of the tap adapter. --tap_adapter.mss_override arg (=auto) The MSS override. --tap_adapter.metric arg (=auto) The metric of the tap adapter. --tap_adapter.ipv4_address_prefix_length arg The tap adapter IPv4 address and prefix length. --tap_adapter.ipv6_address_prefix_length arg The tap adapter IPv6 address and prefix length. --tap_adapter.remote_ipv4_address arg The tap adapter IPv4 remote address. --tap_adapter.arp_proxy_enabled arg (=0) Whether to enable the ARP proxy. --tap_adapter.arp_proxy_fake_ethernet_address arg (=00:aa:bb:cc:dd:ee) The ARP proxy fake ethernet address. --tap_adapter.dhcp_proxy_enabled arg (=1) Whether to enable the DHCP proxy. --tap_adapter.dhcp_server_ipv4_address_prefix_length arg (=9.0.0.0/24) The DHCP proxy server IPv4 address and prefix length. --tap_adapter.dhcp_server_ipv6_address_prefix_length arg (=fe80::/10) The DHCP proxy server IPv6 address and prefix length. --tap_adapter.up_script arg (="") The tap adapter up script. --tap_adapter.down_script arg (="") The tap adapter down script. Switch options: --switch.routing_method arg (=switch) The routing method for messages. --switch.relay_mode_enabled arg (=no) Whether to enable the relay mode. Router options: --router.local_ip_route arg A route to advertise to the other peers. --router.local_dns_server arg A DNS server to advertise to the other peers. --router.client_routing_enabled arg (=yes) Whether to enable client routing. --router.accept_routes_requests arg (=yes) Whether to accept routes requests. --router.internal_route_acceptance_policy arg (=unicast_in_network) The internal route acceptance policy. --router.system_route_acceptance_policy arg (=none) The system route acceptance policy. --router.maximum_routes_limit arg (=1) The maximum count of routes to accept for a given host. --router.dns_servers_acceptance_policy arg (=in_network) The DNS servers acceptance policy. --router.dns_script arg (="") The DNS script. Daemon: -f [ --foreground ] Do not run as a daemon. -s [ --syslog ] Always log to syslog (useful when running with --foreground on OSX with launchd). -p [ --pid_file ] arg A pid file to use. Miscellaneous: --nocolor Disable color output.
Let us now see how we can remove this software from our Linux system.
Uninstalling FreeLAN from the Linux system
In case you, for one reason or another, want to do away with the just-installed software on your system, then here is how to do it.
Issue the following command to remove the FreeLAN architecture from your Linux system:
sudo apt-get remove freelan
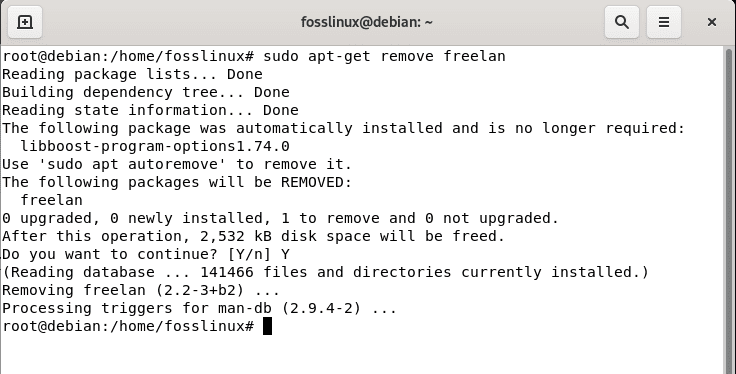
Get remove FreeLAN
Also, you can use this other command to remove the FreeLAN Architecture package along with its dependencies:
sudo apt-get remove --auto-remove freelan
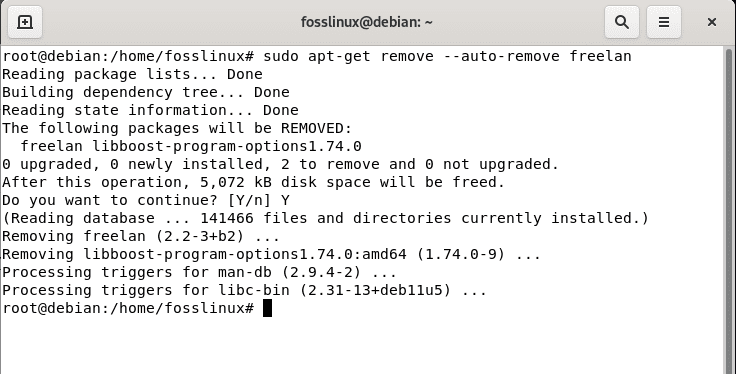
Remove autoremove freelan
The above command will remove FreeLAN Architecture with all the dependent packages that are no longer needed by the system.
This other command should altogether remove FreeLAN architecture and all its configuration files. But remember to use this command carefully, as it deletes all the configuration files and data:
sudo apt-get purge freelan
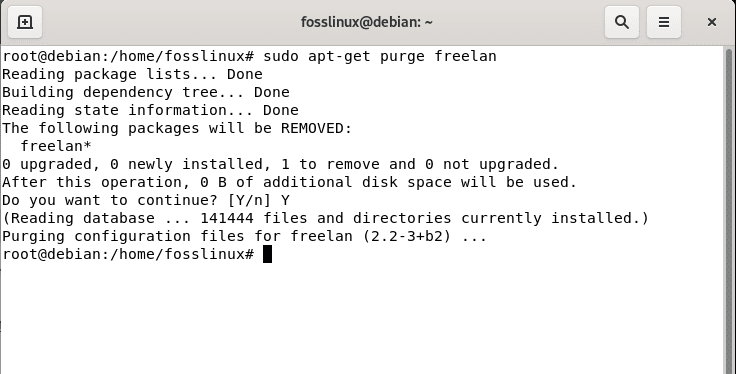
Purge freelan
Alternatively, you can use this other command:
sudo apt-get purge --auto-remove freelan
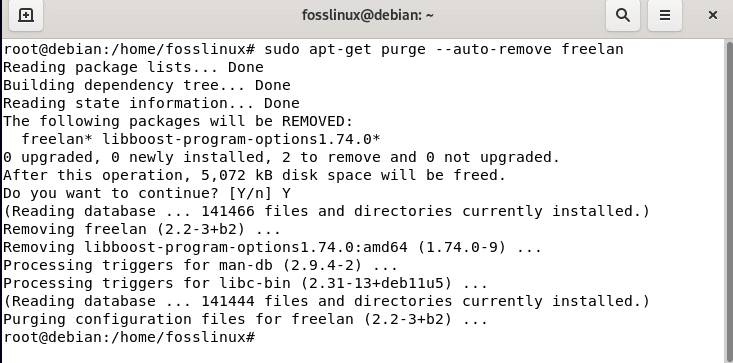
Alternative approach
Wrapping up
And that should do it for you. We have covered the most basic stuff about FreeLAN. We first began with the software’s essential features, then the pros and cons, the installation section, an essential description of FreeLAN functionalities, and concluded with the uninstallation phase. We hope this came in handy!