iptables is a user-space utility software that allows a system administrator to customize the Linux kernel firewall’s IP packet filter rules, which are implemented as various Netfilter modules. The filters are structured into tables with chains of rules governing how network traffic packets are treated. iptables is a powerful utility for configuring port access on your PC or server. It gives the necessary control to specify what network traffic is allowed or denied to the system.
To set up, manage, and analyze the firewall tables of IPv4 and IPv6 packet filter rules in the Linux kernel, system administrators and developers utilize the iptables and ip6tables programs. Unfortunately, any changes performed with these commands are lost when the Linux server is rebooted. As a result, we must persistently preserve those rules across reboots. This article demonstrates how to permanently preserve iptables firewall rules on an Ubuntu Linux system.
Experienced Linux administrators are probably familiar with the annoyance and suffering of a reboot that entirely deletes a system’s iptables rules. This is because, by default, iptables rules do not remain after a reboot. After establishing your system’s iptables rules, you must take one more step to ensure the rules stay in place after a reboot.
Making iptables persistent after reboot on Linux
This guide will illustrate how to make iptables rules durable after rebooting your Ubuntu and Cent OS.
Before we begin, ensure you have specific rules set up on your system. This tutorial assumes that you have already configured the rules with iptables. Type to see a list of rules:
sudo iptables -L

List iptables rules
This should show you the current status of all the access and block rules you’ve set up on your system.
How to save iptables rules on Ubuntu?
Install the iptables-persistent package using the apt package manager to make your iptables rules permanent after reboot:
sudo apt-get install iptables-persistent
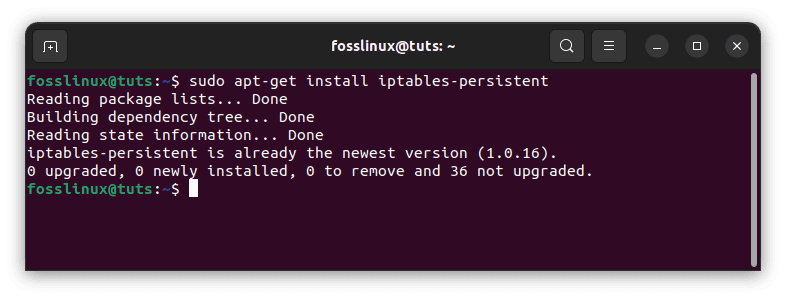
Install iptables-persistent
Any presently mentioned iptables rules would be stored in the IPv4 and IPv6 files indicated below:
/etc/iptables/rules.v4 /etc/iptables/rules.v6
To integrate new rules in your system, just use the iptables command to update persistent iptables. Run the iptables-save command to make modifications permanent after a reboot:
sudo iptables-save > /etc/iptables/rules.v4 sudo ip6tables-save > /etc/iptables/rules.v6
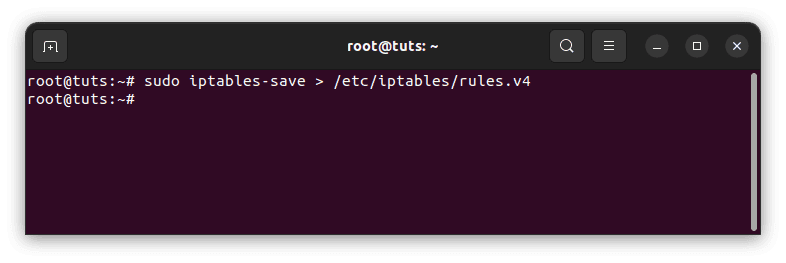
Save iptables rules
To remove persistent iptables rules, open the relevant /etc/iptables/rules.v* file and delete any undesired rules.
How to save iptables rules on CentOS
Install the iptables-services package using the dnf package manager to make your iptables rules persistent after reboot:
sudo dnf install iptables-services
Any current iptables rules will be stored in the IPv4 and IPv6 files listed below:
/etc/sysconfig/iptables /etc/sysconfig/ip6tables
Make sure that the firewalld service is disabled, and the iptables service is enabled in the system by executing the lines of code provided below:
sudo systemctl stop firewalld sudo systemctl disable firewalld sudo systemctl start iptables sudo systemctl enable iptables
You can then use the following command to ensure that the service is running:
sudo systemctl status iptables
To integrate new rules in your system, just use the iptables command to update persistent iptables. Run the iptables-save command to make modifications permanent after a reboot:
sudo iptables-save > /etc/sysconfig/iptables sudo ip6tables-save > /etc/sysconfig/ip6tables
Note: To remove persistent iptables rules, edit the corresponding /etc/sysconfig/iptables or /etc/sysconfig/ip6tables file and delete any lines that include undesired rules.
Conclusion
This post taught you how to permanently save and restore iptables rules on Linux, specifically on Debian/Ubuntu or CentOS/RHEL/Rocky/Alma Linux systems. Remember to configure the Linux firewall with only one service. Many systems now have their own iptables front end, such as firewalld or ufw, which makes the firewall more user pleasant and saves your rules by default. I hope you are now able to make your iptables persistent. Thanks for reading.